AFRICA UNODC CTF 2022
AFRICA UNODC CTF was organized by DFIRScience,UNODC and alot of people.This CTF was good,thanks to organizers and i really learn alot that mostly i didn’t know before. The Writeup for Week one was written by two people, me,Username blackninja23 and my collegue, Username hashghost
WEEK 01 UNODC
SCENARIO: GIVEN
1
2
3
4
5
### Week 1
A victim, Artemis Nuru, entered a local police department and claimed that "My computer was hacked. They stole all my crypto and encrypted my files. Now they're asking for more money." The victim had his laptop still running when he gave it to investigators. The forensic lab collected a RAM image using AVML and a disk image in Expert Witness Format (E01) using FTK Imager on Tsurugi Linux. **The victim claims that he does not have a phone.**
- Week 1 Linux Disk and Memory Images: [torrent](https://archive.org/download/AfricaDFIRCTF22WK1/AfricaDFIRCTF22WK1_archive.torrent)
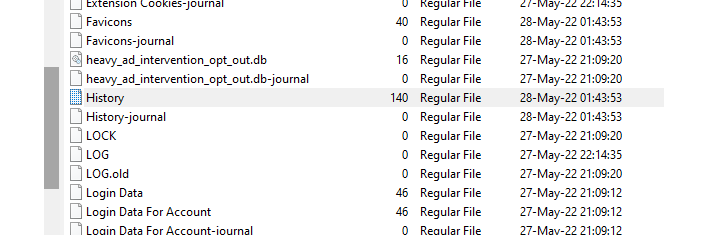
You can download the torrent for Week 1 Linux Disk and Memory Images and it highly recommend you download the datasets using the BitTorrent protocol. After you download,you will have this file as shown below 
PREREQUISITE
- Having Windows 10 or 8 or 7(Your Own Choice)
- That Windows with FTK Imager or Autopsy or both
- Having ewf-tools(in Kali,it is preinstalled)
- Having avml AVML
- Also even better having Tsurugi Linux
Hash Master
FIRST WAY
First before anything, we need to verify what i download is correctly to what was taken/ collected Checking for disk, we will use ewfverify to check it
ewfverify -d sha1 Disk001.E01
Output(last 6 lines)
1
2
3
4
5
6
MD5 hash stored in file: 39e369b5498fdef0814ddf15b3e610af
MD5 hash calculated over data: 39e369b5498fdef0814ddf15b3e610af
SHA1 hash stored in file: 9bbacb877e5fe4a15bf03b2ee01b18507fe9b165
SHA1 hash calculated over data: 9bbacb877e5fe4a15bf03b2ee01b18507fe9b165
ewfverify: SUCCESS
In which it is same as hash that file ‘Disk001.E01.txt’ has it
➜ 14257525-E001-SDA cat Disk001.E01.txt
Case Information:
Acquired using: ADI3
Case Number: 14257525
Evidence Number: E001
Unique description: E001 hard disk
Examiner: DFIRScience
Notes:
The needed Output
1
2
3
[Computed Hashes]
MD5 checksum: 39e369b5498fdef0814ddf15b3e610af
SHA1 checksum: 9bbacb877e5fe4a15bf03b2ee01b18507fe9b165
ANOTHER WAY You could just open case with either ftk imager or autopsy and read the hash from them
ACTION TO BE DONE BEFORE WE CONTINUED
Before we continue after verify it, we need to mount our disk so as to play with it as we answer question followed. Move Your disk image to Tsurugi Linux First we need to check in device mapper if there is logic volumes exist in /dev/mapper
1
2
3
4
5
6
tsurugi@lab:~/DISK01$ ls -la /dev/mapper
total 0
drwxr-xr-x 2 root root 60 Jun 1 03:41 .
drwxr-xr-x 18 root root 13760 Jun 1 16:14 ..
crw------- 1 root root 10, 236 Jun 1 03:42 control
tsurugi@lab:~/DISK01$
in our system there is no logic volumes exist
Second step, we need to check what kind of file is this so as to know how to mount it
1
2
3
4
tsurugi@lab:~/DISK01$ file Disk001.E01
Disk001.E01: EWF/Expert Witness/EnCase image file format
tsurugi@lab:~/DISK01$
The format is expert witness format Short commands
1
2
3
4
5
sudo ewfmount Disk001.E01 /mnt/ewf1 #whereDISK001.E01islocated#
sudo kpartx -a /mnt/ewf1/ewf1
sudo lvscan
sudo mount /dev/vgmint/root /mnt/c #(resultfromlvscan that /dev/vgmint/root)#
chroot /mnt/c
Third step, we need to mount it and our best tool is ewfmount
1
2
3
4
5
tsurugi@lab:~/DISK01$ sudo ewfmount Disk001.E01 /mnt/ewf1
[sudo] password for tsurugi:
ewfmount 20210807
We can verify by checking if file ‘ewf1’ was created
1
2
3
4
5
6
tsurugi@lab:~/DISK01$ sudo ls -la /mnt/ewf1
total 4
dr-xr-xr-x 2 root root 0 Jun 1 16:37 .
drwxr-xr-x 44 root root 4096 Nov 14 2021 ..
-r--r--r-- 1 root root 21474836480 Jun 1 16:37 ewf1
Also check by type command ‘mount’(no need of root)
mount
Output(check last line)
1
/dev/fuse on /mnt/ewf1 type fuse (rw,nosuid,nodev,relatime,user_id=0,group_id=0)
Fourth step, we need to access partitions inside a physical device by using a tool called kpartx
sudo kpartx -a /mnt/Disk001_W01/ewf1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
tsurugi@lab:~/DISK01$ sudo kpartx -a /mnt/ewf1/ewf1
[sudo] password for tsurugi:
tsurugi@lab:~/DISK01$ ls -la /dev/mapper
total 0
drwxr-xr-x 2 root root 160 Jun 1 16:41 .
drwxr-xr-x 19 root root 13880 Jun 1 16:41 ..
crw------- 1 root root 10, 236 Jun 1 03:42 control
lrwxrwxrwx 1 root root 7 Jun 1 16:41 loop6p1 -> ../dm-0
lrwxrwxrwx 1 root root 7 Jun 1 16:41 loop6p2 -> ../dm-1
lrwxrwxrwx 1 root root 7 Jun 1 16:41 loop6p5 -> ../dm-2
lrwxrwxrwx 1 root root 7 Jun 1 16:41 vgmint-root -> ../dm-3
lrwxrwxrwx 1 root root 7 Jun 1 16:41 vgmint-swap_1 -> ../dm-4
tsurugi@lab:~/DISK01$ sudo lvs
lvs lvscan
tsurugi@lab:~/DISK01$ sudo lvscan
ACTIVE '/dev/vgmint/root' [<18.51 GiB] inherit
ACTIVE '/dev/vgmint/swap_1' [976.00 MiB] inherit
tsurugi@lab:~/DISK01$
After that,we then mount /dev/vgmint/root to /mnt/c so as to play with it
1
2
3
4
tsurugi@lab:~/DISK01$ sudo mount /dev/vgmint/root /mnt/c
mount: /mnt/c: WARNING: device write-protected, mounted read-only.
tsurugi@lab:~/DISK01$
Then we move to /mnt/c
1
2
3
4
5
6
tsurugi@lab:~/DISK01$ cd /mnt/c
tsurugi@lab:/mnt/c$ ls
bin cdrom etc lib lib64 lost+found mnt proc run snap sys usr
boot dev home lib32 libx32 media opt root sbin srv tmp var
tsurugi@lab:/mnt/c$
Let move to our mount as if we are in it
1
2
3
4
root@lab:/home/tsurugi/DISK01# chroot /mnt/c
root@lab:/#
root@lab:/#
Code breaker
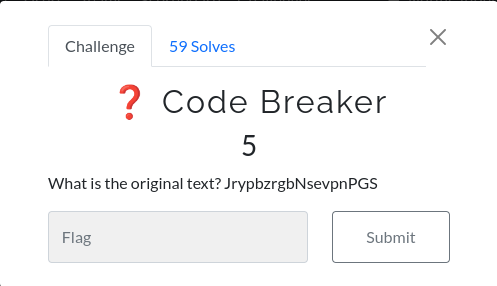
We have text JrypbzrgbNsevpnPGS that seems need to decode.We can use site like dcode.fr to recognize the text and it show that it is rot13. You can use the same site to decode it
1
2
3
4
5
6
7
8
└─$ python3
Python 3.10.4 (main, Mar 24 2022, 13:07:27) [GCC 11.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import codecs
>>> codecs.encode('JrypbzrgbNsevpnPGS', 'rot_13')
'WelcometoAfricaCTF'
>>>
Our flag is WelcometoAfricaCTF
What do we have here?
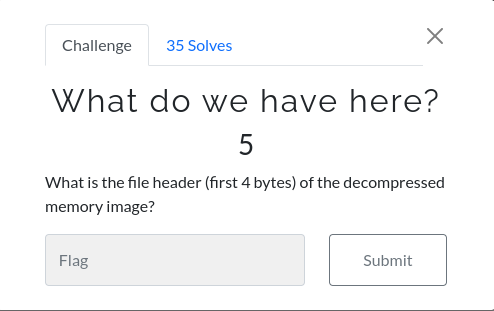
We also have a memory image as we given after download it.But it has been compressed via snappy. Let first observe the header with command ‘xxd’
1
2
3
4
5
6
7
8
9
└─$ xxd E001.lime.snappy |head
00000000: 4156 4d4c 0200 0000 0010 0000 0000 0000 AVML............
00000010: ffef 0900 0000 0000 0000 0000 0000 0000 ................
00000020: ff06 0000 734e 6150 7059 0027 1200 4d80 ....sNaPpY.'..M.
00000030: b255 8080 0400 00fe 0100 fe01 00fe 0100 .U..............
00000040: fe01 00fe 0100 fe01 00fe 0100 fe01 00fe ................
00000050: 0100 fe01 00fe 0100 fe01 00fe 0100 fe01 ................
00000060: 00fe 0100 fe01 00fe 0100 fe01 00fe 0100 ................
We see the first 4 bytes ‘AVML’ then we search it online, we come to avml github but we can use Tsurugi Linux for this issue in which avml and avml-convert as our tool is already installed. Use avml-convert to convert it to lime
1
2
3
4
tsurugi@lab:~/MEM01$ ls
E001.lime.snappy
tsurugi@lab:~/MEM01$ avml-convert ./E001.lime.snappy ./E001.lime
Observe lime with xxd command
1
2
3
tsurugi@lab:~/MEM01$ xxd E001.lime |head
00000000: 454d 694c 0100 0000 0010 0000 0000 0000 EMiL............
we have our first 4 bytes and it is our flag, it is EMiL
Part of the way
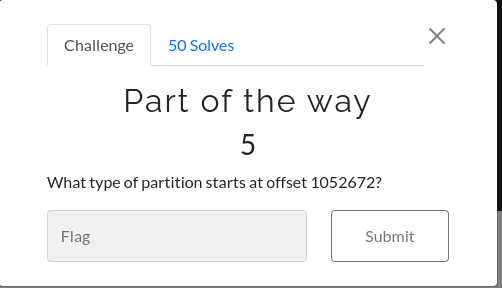
Basically, it is to know which partition start at that offset. We can use a tool called fdisk or mmls
1
root@lab:/home/tsurugi/MEM01# fdisk -l
Output(middle lines)
1
2
3
4
5
6
7
8
9
10
11
12
Disk /dev/loop6: 20 GiB, 21474836480 bytes, 41943040 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0x1bf47736
Device Boot Start End Sectors Size Id Type
/dev/loop6p1 * 2048 1050623 1048576 512M b W95 FAT32
/dev/loop6p2 1052670 41940991 40888322 19.5G 5 Extended
/dev/loop6p5 1052672 41940991 40888320 19.5G 8e Linux LVM
We can see /dev/loop6p5 the offset has start at 1052672 in which it is Linux LVM Using mmls
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@lab:/home/tsurugi/DISK01# mmls Disk001.E01
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
000: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
001: ------- 0000000000 0000002047 0000002048 Unallocated
002: 000:000 0000002048 0001050623 0001048576 Win95 FAT32 (0x0b)
003: ------- 0001050624 0001052671 0000002048 Unallocated
004: Meta 0001052670 0041940991 0040888322 DOS Extended (0x05)
005: Meta 0001052670 0001052670 0000000001 Extended Table (#1)
006: 001:000 0001052672 0041940991 0040888320 Linux Logical Volume Manager (0x8e)
007: ------- 0041940992 0041943039 0000002048 Unallocated
Also from this, we can as well ,it start from 0001052672 in which it is Linux Logical Volume Manager then our flag is Linux Logical Volume Manager
Everyone Likes Cartoons
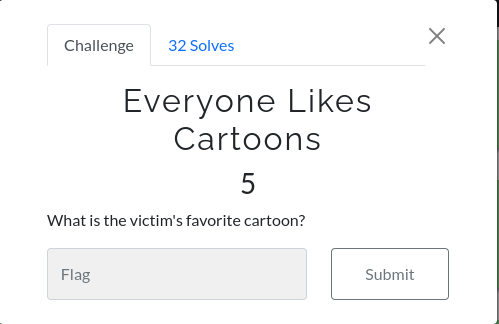
After i see this, i decided to go and check Download but also we see the username of this user is bighero in which it is also name of animation. but remember to follow up there if you want to interact with it
1
2
3
4
5
6
7
8
9
root@lab:/# ls /home/
bighero
root@lab:/# su bighero
bighero@lab:/$ cd ~/Downloads/
bighero@lab:~/Downloads$ ls
Big-Hero-7.jpg i2pinstall_1.8.0.jar tor-browser-linux64-11.0.13_en-US.tar.xz
google-chrome-stable_current_amd64.deb icecat-17.0.1-64bit.tar.gz
bighero@lab:~/Downloads$
We can see some few files we were downloaded. let deal with that pic 
With name, you can think it is big hero 7 but after google it, we can confirm it is not yet out and we have big hero 6 Let dig deep Logic
Let us have our logic straigth
User did download icecat, google chrome, tor browser and other browser that we dont see here it is mozilla firefox meaning that we should check it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
bighero@lab:~$ cd .mozilla/
bighero@lab:~/.mozilla$ ls
extensions firefox icecat
bighero@lab:~/.mozilla$ cd firefox/
bighero@lab:~/.mozilla/firefox$ ls
8bf96zi6.default 'Crash Reports' installs.ini jfnvehc5.default-release 'Pending Pings' profiles.ini
bighero@lab:~/.mozilla/firefox$ cd jfnvehc5.default-release/
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release$ ls
addons.json cookies.sqlite gmp places.sqlite sessionstore.jsonlz4
addonStartup.json.lz4 crashes gmp-gmpopenh264 prefs.js shield-preference-experiments.json
AlternateServices.txt datareporting gmp-widevinecdm protections.sqlite SiteSecurityServiceState.txt
bookmarkbackups extension-preferences.json handlers.json saved-telemetry-pings storage
broadcast-listeners.json extensions key4.db search.json.mozlz4 storage.sqlite
cert9.db extensions.json lock security_state times.json
compatibility.ini favicons.sqlite minidumps serviceworker.txt webappsstore.sqlite
containers.json features permissions.sqlite sessionCheckpoints.json xulstore.json
content-prefs.sqlite formhistory.sqlite pkcs11.txt sessionstore-backups
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release$
Let check what was entered in forms when he was browsing and we can check our file called formhistory.sqlite
1
sqlitebrowser /mnt/c/home/bighero/.mozilla/firefox/jfnvehc5.default-release/formhistory.sqlite
As you can see when you open this file and browse the “moz_formhistory” table, there are loads of entries which give you a bit of insight into how this feature works. 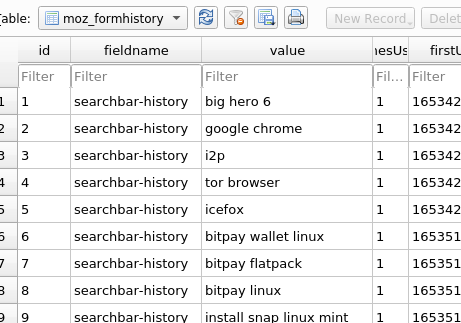
We can see user search for big hero 6 Also User use name of bighero6 as hostname
1
2
3
4
5
bighero@lab:~$ cat /etc/hostname
bighero6
bighero@lab:~$
bighero@lab:~$
Then our flag is bighero6
History 👀
After awhile, we discover it was firefox browser, by view under storage then default
Check the methodology down
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
bighero@lab:~$ cd .mozilla/firefox/
bighero@lab:~/.mozilla/firefox$ ls
8bf96zi6.default 'Crash Reports' installs.ini jfnvehc5.default-release 'Pending Pings' profiles.ini
bighero@lab:~/.mozilla/firefox$ cd jfnvehc5.default-release/storage/^C
bighero@lab:~/.mozilla/firefox$ cd
bighero@lab:~$
bighero@lab:~$ cd .mozilla/firefox/jfnvehc5.default-release/storage/
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage$ ls -la
total 148
drwxr-xr-x 5 bighero bighero 4096 May 24 20:01 .
drwx------ 15 bighero bighero 4096 May 29 02:01 ..
drwxr-xr-x 16 bighero bighero 4096 May 29 01:59 default
-rw-r--r-- 1 bighero bighero 131072 May 24 20:01 ls-archive.sqlite
drwxr-xr-x 3 bighero bighero 4096 May 24 20:01 permanent
drwxr-xr-x 2 bighero bighero 4096 May 24 20:01 temporary
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage$ cd default/
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage/default$ ls
https+++apps.apple.com https+++snapcraft.io https+++www.npr.org
https+++en.wikipedia.org https+++support.bitpay.com https+++www.quora.com
https+++github.com https+++swag.dfir.science https+++www.reclaimcrypto.com
https+++pluto.tv https+++www.comparitech.com 'moz-extension+++8e726fde-69d3-403a-b0a5-403310e2f660^userContextId=4294967295'
https+++prebid.a-mo.net https+++www.google.com
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage/default$ cd https+++pluto.tv/
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage/default/https+++pluto.tv$ ls -la
total 16
drwxr-xr-x 3 bighero bighero 4096 May 24 22:50 .
drwxr-xr-x 16 bighero bighero 4096 May 29 01:59 ..
drwxr-xr-x 2 bighero bighero 4096 May 26 12:34 ls
-rw-rw-r-- 1 bighero bighero 54 May 26 13:56 .metadata-v2
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage/default/https+++pluto.tv$ cd ls
bighero@lab:~/.mozilla/firefox/jfnvehc5.default-release/storage/default/https+++pluto.tv/ls$ ls -la
total 20
drwxr-xr-x 2 bighero bighero 4096 May 26 12:34 .
drwxr-xr-x 3 bighero bighero 4096 May 24 22:50 ..
-rw-r--r-- 1 bighero bighero 8192 May 26 12:34 data.sqlite
-rw-rw-r-- 1 bighero bighero 12 May 26 12:34 usage
We have our browser which it is firefox but you can view data.sqlite, if you prefer to know more what was done in the pluto.tv Our flag is firefox
฿
We can look at also that formhistory from earlier as it contain things we have searched in forms

and see most of time,they mention bitpay, with little google,
1
BitPay is a bitcoin payment service provider headquartered in Atlanta, Georgia, United States. It was founded in May 2011 by Tony Gallippi and Stephen Pair. BitPay provides Bitcoin and Bitcoin Cash payment processing services for merchants.
we undestand it is our flag bitpay
So Dark
We review back to our Downloads from user bighero
1
2
3
bighero@lab:~/Downloads$ ls
Big-Hero-7.jpg i2pinstall_1.8.0.jar tor-browser-linux64-11.0.13_en-US.tar.xz
google-chrome-stable_current_amd64.deb icecat-17.0.1-64bit.tar.gz
see browsers that were downloaded and after review, we found something in icecat and also i2p and tor are darkwebs in our machine but first let review how did victim access darkweb
1
sqlitebrowser /mnt/c/home/bighero/.mozilla/icecat/wk4ls5vn.default/formhistory.sqlite
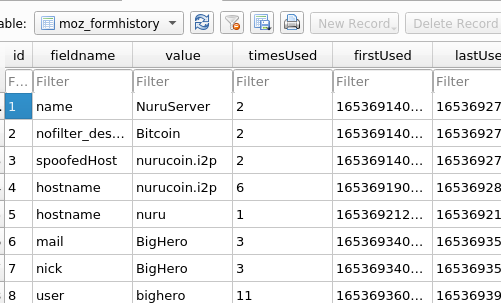
we can see user access nurucoin.i2p and others i2p in which mostly many were observed in Autopsy .We can understand i2p by understand eepsite
1
An eepsite is a website that is hosted anonymously, a hidden service which is accessible through your web browser. It can be accessed by setting your web browser’s HTTP proxy to use the I2P web proxy (typically it listens on localhost port 4444), and browsing to the site.
Well, Our flag is i2p
HISTORY 👀👀
This is browser history and every browser have default location to store history, in this case user used chrome browser to access the web that let him install bitcoin wallet. This file can be found on path ~/.config/google-chrome/Default/History. This file can be accessed by using both AccessData FTK Imager or by using tsurugi. This file is in sqlite format then we have to export it and read it with SQlite database browser through the following steps.
Navigate up History file and export it.
Open the file with SQlite databse browser
1
2
3
4
5
6
┌──(gemstone㉿hashghost)-[~/C7F5/unodc]
└─$ ls
diskImage History memoryImage setups
┌──(gemstone㉿hashghost)-[~/C7F5/unodc]
└─$ sqlitebrowser History
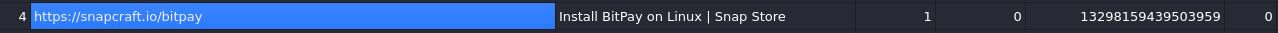
Select table urls When is SQlite database browser is open navigate to Browse Data and change table from to urls and copy https://snapcraft.io/bitpay 'last_visit_time.
This time is in the chrome format and not human readable.
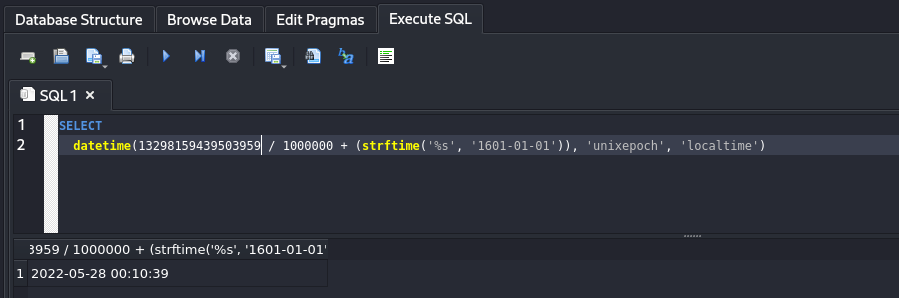
Convert the time On stackoverflowthere is a query which can be executed by SQlite database browser. then we will use the following query to convert.
1
2
SELECT
datetime(13029358986442901 / 1000000 + (strftime('%s', '1601-01-01')), 'unixepoch', 'localtime')
Result
I’m rich! …nevermind.
Once again this question involves the browsing history but the only difference is that it was performed o top of anonymous network i2p. The file can be accessed on the following path ~/.i2p/eepsite/docroot/ and 3 files can be found.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
bighero@lab:~/.i2p/eepsite/docroot$ ls
favicon.ico index.html robots.txt
bighero@lab:~/.i2p/eepsite/docroot$ cat index.html
<html>
<head>
<meta http-equiv="refresh" content="1;url=/help/" />
<meta http-equiv="pragma" content="no-cache">
<meta http-equiv="cache-control" content="no-cache">
<title>Bitcoin</title>
</head>
<body>
Send me bitcoin. I want to buy a lambo.
bc1qkzqng3jtg87syx3apftj7q0tp686hm48mtwu2c
</body>
</html>
bighero@lab:~/.i2p/eepsite/docroot$
Then on opening index.html then we can find find the following ink bc1qkzqng3jtg87syx3apftj7q0tp686hm48mtwu2c which is the answer of the question.
Little weird
It seems that user installed some different tools on his machine and one of them was ncat tool. This is log and can be found on /var/log/apt/ and then read the history.log file.
1
2
3
4
5
6
7
8
9
10
bighero@lab:/var/log/apt$ cat history.log | grep ncat -C 6
Commandline: /usr/bin/apt install i2p
Requested-By: bighero (1000)
Install: libjson-simple-java:amd64 (2.3.0-1, automatic), libjbigi-jni:amd64 (1.8.0-1ubuntu1, automatic), libtomcat9-java:amd64 (9.0.31-1ubuntu0.2, automatic), libgetopt-java:amd64 (1.0.14+dfsg-4, automatic), i2p:amd64 (1.8.0-1ubuntu1), famfamfam-flag-png:amd64 (0.1-3, automatic), libjetty9-java:amd64 (9.4.26-1, automatic), i2p-router:amd64 (1.8.0-1ubuntu1, automatic), libservice-wrapper-jni:amd64 (3.5.30-1ubuntu1, automatic), libtaglibs-standard-spec-java:amd64 (1.2.5-2, automatic), libservice-wrapper-java:amd64 (3.5.30-1ubuntu1, automatic), service-wrapper:amd64 (3.5.30-1ubuntu1, automatic), libeclipse-jdt-core-java:amd64 (3.18.0+eclipse4.12-1, automatic), libtaglibs-standard-jstlel-java:amd64 (1.2.5-2, automatic), libtaglibs-standard-impl-java:amd64 (1.2.5-2, automatic)
End-Date: 2022-05-27 22:17:34
Start-Date: 2022-05-28 23:51:39
Commandline: /usr/bin/apt install ncat
Install: ncat:amd64 (7.80+dfsg1-2build1), liblua5.3-0:amd64 (5.3.3-1.1ubuntu2, automatic)
End-Date: 2022-05-28 23:51:42
Then through this log it is clear that user installed ncat at 2022-05-28 23:51:39
EEP!
To access or use eepsite user must do some configurations on i2p network so that he/she can access the internet and one of the main things he must specify hostname. Something important to note is that all i2p host-name ends with ## .i2p extensions. We managed to do this question by using Autopsy tool through the following steps.
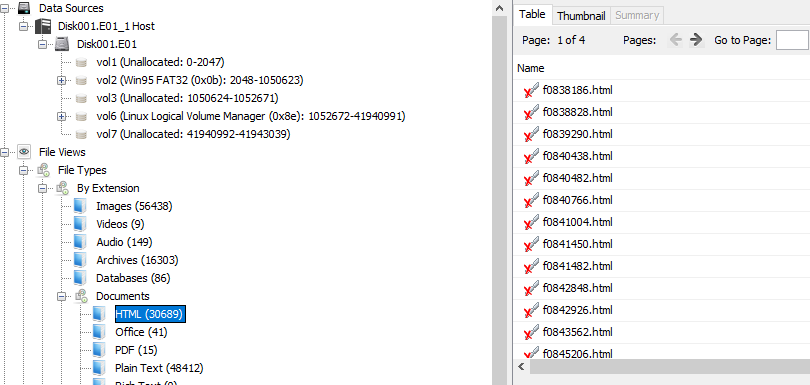
Select HTML files On autopsy, navigate to File Types–>Documents–>HTML
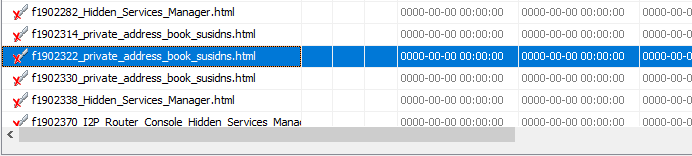
Open files with susidns.html On listing view of autopsy, click the second file with susidns.html name
Result Below the listing view you will see the a picture appearing as picture, scroll down to Hostname
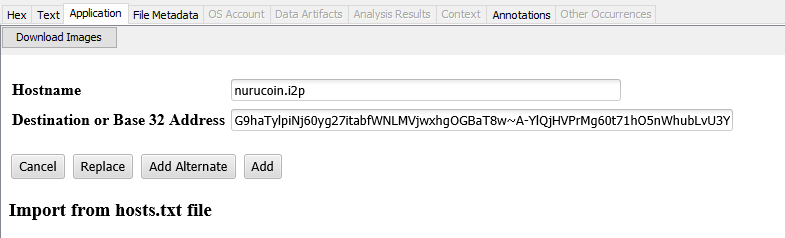
Then user’s eepsite hostname is nurucoin.i2p
You shall pass!
This is one among of the tough easy question hahahaha, just kidding. we heard some people crack the password in some days and still got nothing but we solve this question in unexpected way. On scenario, user handled his machine to the police station while it was still on then according to this the password files and some of data were captured by memory and did not appear in disk image. We can use memory dump to its fully potential by dump strings from memory and crack our password that user had from /etc/shadow
1
2
3
4
5
6
7
┌──(blackninja23㉿arena)-[~/Documents/AFRICACTF2022UNODC/AfricaDFIRCTF22WK1/14257525-E001-MEM]
└─$ strings E001.lime|sort|uniq > dumpstrings.txt 130 ⨯
┌──(blackninja23㉿arena)-[~/Documents/AFRICACTF2022UNODC/AfricaDFIRCTF22WK1/14257525-E001-MEM]
└─$ hashcat -m 1800 hash.txt dumpstrings.txt
hashcat (v6.2.5) starting
Our password for user bighero was cracked
1
2
$6$PTFlDR.FQlFBOkvk$mzA5KAHYfZmke2Q7WBtI9fFy5kScKiWNTnSk/0cvXQcRpt0/5eR85Oe5/JM4EXoRASWqGPpcd6YcSJd0xehD9.:$Hero!!
password is $Hero!! and it is our answer
Trying to be sneaky, eh?
As we all know that in linux file-system, sometimes additional application tends to be configured in opt directory, then user configured eepsites in opt directory together with its binary. This can performed by AccessData FTK Imager or tsurugi
Navigate to /opt/icecat directory
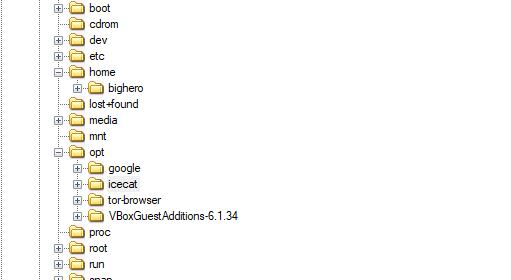
and opening it
This is the binary that is running the eepsite so the correct answer here is /opt/icecat/icecat